FIDO2
FIDO2
Fast Identity Online 2 (FIDO2), is an open authentication standard developed by the FIDO Alliance. In this section, FIDO2 supported devices can be configured for the second factor authentication in the webui as well as in the ezsh shell.
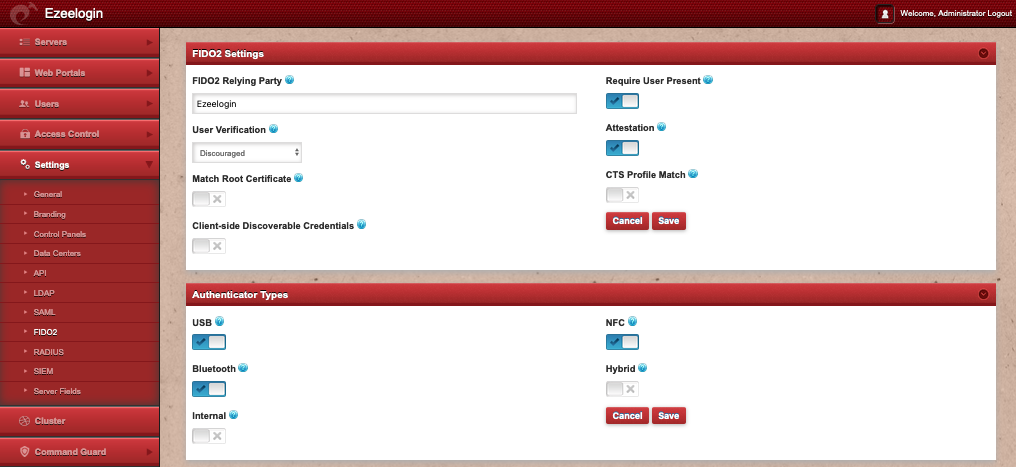
FIDO2 Settings
FIDO2 Relying Party The Relying Party name
Require User Present If the device should check for the presence of the user (ex: Pressing a button on the keyboard)
User Verification
- required: If user verfication is required (e.g by pin), the operation will fail if the response does not have the UV flag
- preferred: user verfication is prefered, the operation will not fail if the response does not have the UV flag
- discouraged: user verification should not be employed as to minimize the user interaction during the process.
Attestation It refers to the capability of a FIDO authenticator to provide a cryptographic proof about its model. This allows to verify that the authenticator that generated the public key is really the specific model of authenticator it claims to be.
Match Root Certificate Accept only if the root certificate matches
CTS Profile Match Accept only if the device is approved as Google-certified Android device.
Client-Side Discoverable Credentials if It means that the private key and associated metadata is stored n persistent memory on the authenticator, instead of encrypted and stored on the relying party server. This is mainly user for username-less login, which is not supported in Ezeelogin.
- Warning: Most client-side modules and authenticators do not allow to delete single client side credentials. You have to reset the full device to remove the credentials again
Authenticator Types
USB Accept USB authenticator devices
NFC Accept NFC authenticator devices
Hybrid Accept passkeys via mobile devices
Bluetooth Accept Bluetooth authenticator devices
Internal Accept passkeys on the device - Windoes Hello, Andriod SafetyNet, Apple, etc.
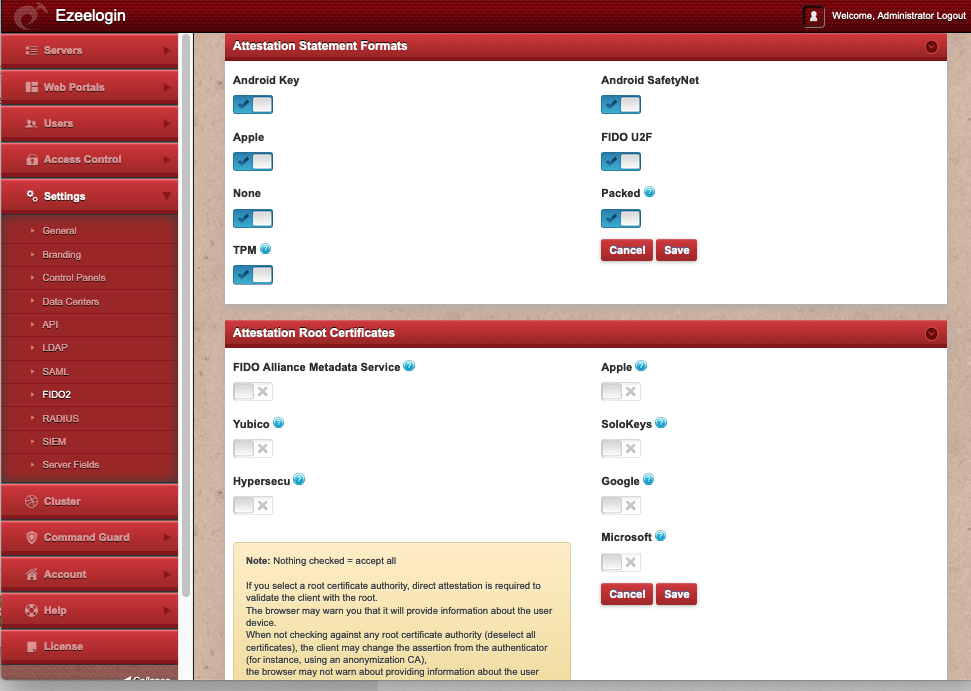
Attestation Statement Formats
Andriod Key
Android SafetyNet
Apple
FIDO U2F
NONE
Packed A generic attestation format that is commonly used by the devices whose sole function is as a FIDO2 authenticator, such as security keys.
TPM
Attestation Root Certificates
FIDO Alliance Metadata service Accept the keys signed by root certificates from FIDO Alliance Metadata Service (MDS): https://fidoalliance.org/metadata/
Apple Accept keys signed by Apple root certificate authority
Yubico Accept keys signed by Yubico root certificate authority
SoloKeys Accept keys signed by SoloKeys root certificate authority
HyperSecu Accept keys signed by HyperSecu root certificate authority
Google Accept keys signed by Google root certificate authority
Microsoft Accept keys signed by Microsoft root certificate authority