SAML
SAML
Configure SAML authentication for the web interface. Once this is configured, set the WebPanel Authentication to SAML and users in your SAML Account server can login.Note, ensure that PHP DOM module is installed.
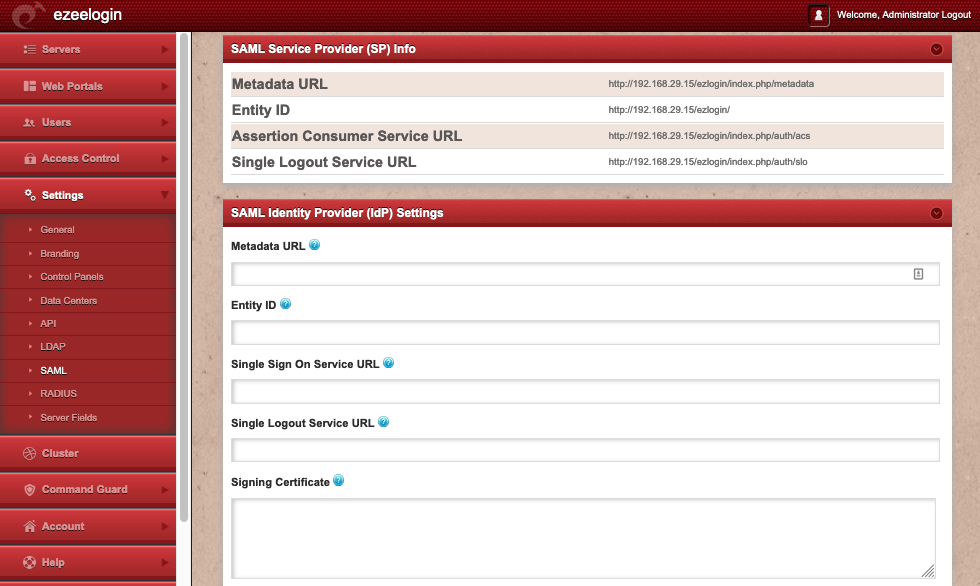
- Metadata URL Specify URL of the SAML service in use and click fetch below and the remaining configuration variables should be auto filled.
- Entity ID Identifier of the lDP entity (must be a URI)
- Single Sign On Service URL Provide the URL for 'HTTP-Redirect' binding
- ID Single Sign On Service URL Provide the URL for 'HTTP-Redirect' binding
- Single Logout Service URL Provide the URL for 'HTTP-Redirect' binding
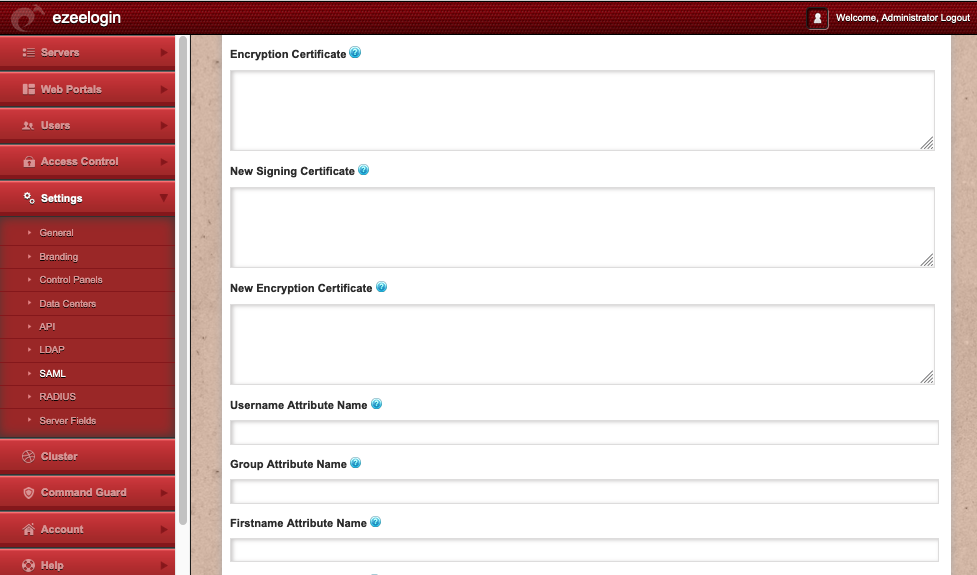
- Signing Certificate The X509 certificate ldP uses for signing
- Encryption Certificate The X509 certificate ldP uses for encryption, in case a different one is used. (Optional)
- New Signing Certificate If the ldP is under the key roll over phase, add the new signing certificate. (Optional)
- New Encryption Certificate If the ldP is under the key roll over phase, add the new Encrytpion Certificate. (Optional)
- Username Attribute Name Name of the saml attribute for username. This attribute value would be used as username during autocreation of gateway user account.
- Group Attribute Name Name of the saml attribute for groupname. A group with the exact same name should be added in usergroup for auto group assignment. If there are multiple matching usergroups, then usergroup would be assigned based on the priority values.
- Firstname Attribute Name Name of the saml attribute for the users Firstname. This attribute value would be used as the firstname when the user is autocreated in Ezeelogin.
- Lastname Attribute Name Name of the saml attribute for the users Lastname. This attribute value would be used as the lastname when the user is autocreated in Ezeelogin.
Azure AD Settings
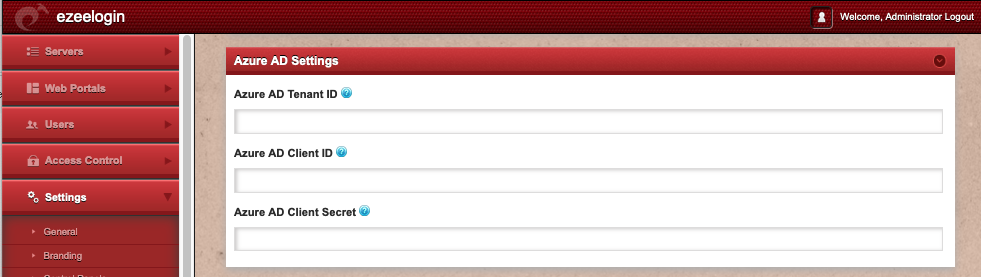
Azure AD Tenant ID Azure AD tenant id from which the users group name has to be fetched from Azure AD.
Azure AD Client ID Azure AD client application id for accessing Microsoft graph API.
Azure AD Client Secret Azure AD client application secret for accessing Microsoft Graph API.
Secondary Node SAML IdP Settings ( Optional)
The secondary node can be authenticated by another IdP provider. An application needs to be created in the IdP provider and the users added into the SAML application. Specify the parameters as described above.
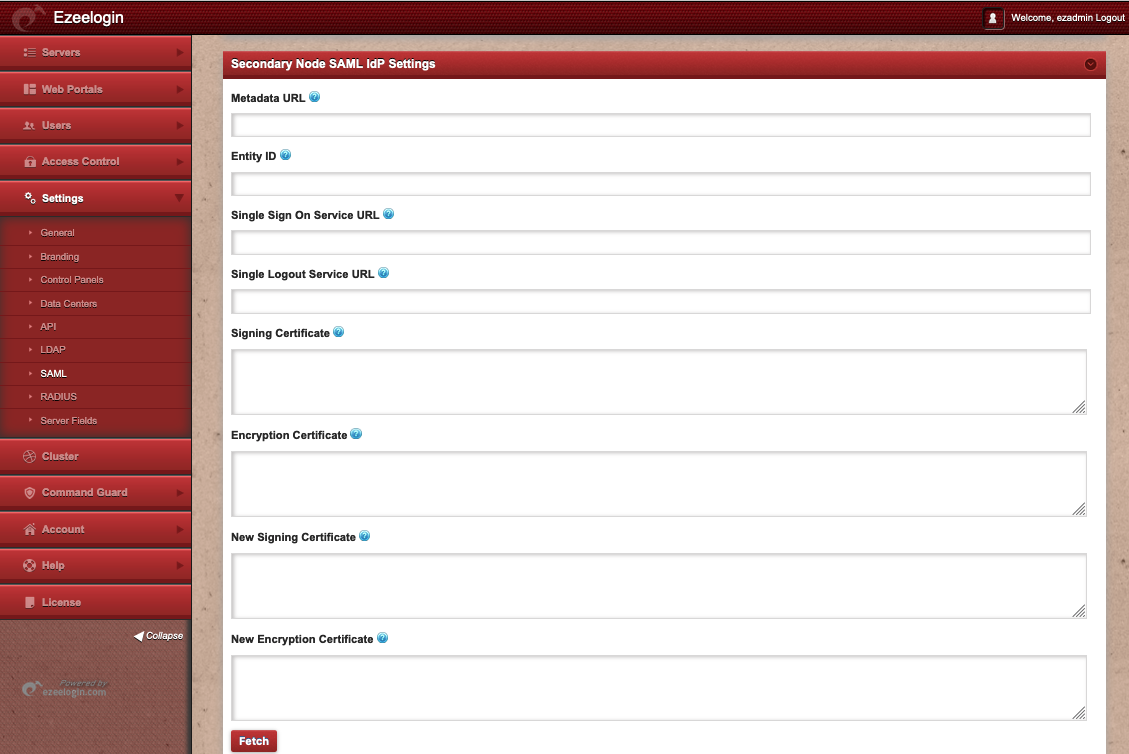
- Metadata URL Specify URL of the SAML service in use and click fetch below and the remaining configuration variables should be auto filled.
- Entity ID Identifier of the lDP entity (must be a URI)
- Single Sign On Service URL Provide the URL for 'HTTP-Redirect' binding
- ID Single Sign On Service URL Provide the URL for 'HTTP-Redirect' binding
- Single Logout Service URL Provide the URL for 'HTTP-Redirect' binding
- Signing Certificate The X509 certificate ldP uses for signing
- Encryption Certificate The X509 certificate ldP uses for encryption, in case a different one is used. (Optional)
- New Signing Certificate If the ldP is under the key roll over phase, add the new signing certificate. (Optional)
- New Encryption Certificate If the ldP is under the key roll over phase, add the new Encrytpion Certificate. (Optional)
Advanced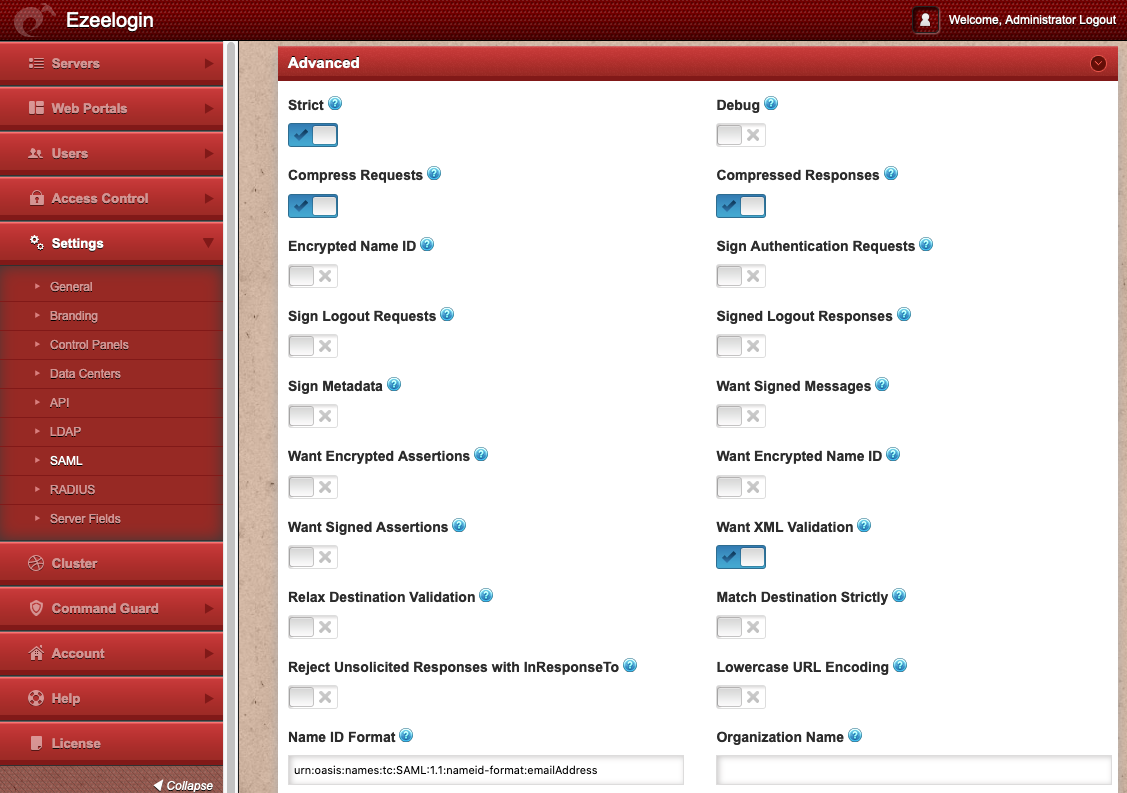
- Strict The SAML authentication would be strict and will reject unsigned or unencrypted messages.
- Debug Enable it for detailed logs.
- Compress Requests Enable it to compress SAML requests.
- Compressed Responses The Enable it to compress the SAML responses.
- Encrypted Name ID Indicates that the NAME ID send from Ezeelogin is encrypted
- Sign Authentication Requests Enable it to sign authentication requests.
- Sign Logout Requests Enable it to sign logout requests.
- Singed Logout Responses Enable it to sign logout responses
- Sign Metadata Enable it to sign the metadata. Requires the service provider certificate and key
- Want Signed Messages Enable it so that only signed messages are accepted
- Want Encrypted Assertions Enable it so that only encrypted elements are accepted
- Want XML Validation Indicates if the SP will validate all received xmls. (In order to validate the xml, 'strict' and 'wantXMLValidation' must be enabled)
- Relax Destination Validation If enabled, SAMLResponses with an empty value at its Destination attribute will not be rejected for this fact.
- Match Destination Strictly if enabled, Destination URL should strictly match to the address to which the response has been sent. Note that if 'Relax Destination Validation' is enabled, an empty Destintation will be accepted.
- Reject Unsolicited Responses with InResponseTo If enabled, SAMLResponses with an InResponseTo value will be rejected if no AuthNRequest ID is provided to the validation method.
- Lowercase URL Encoding ADFS URL-Encodes SAML data as lowercase, and the Ezeelogin by default uses uppercase. Enable this for ADFS compatibility on signature verification.
- Name ID Format Specifies the constraints on the name identifier to be used to represent the requested subject.
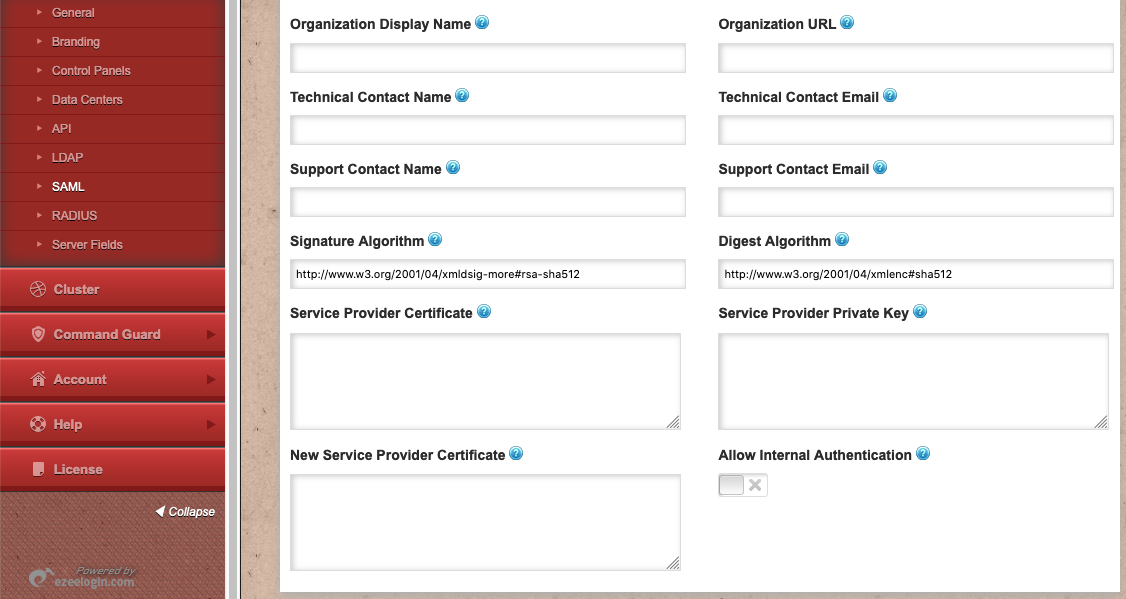
- Organization Name Alias or display name for the organization.
- Organization Display Name Specifies the constraints on the name identifier to be used to represent the requested subject.
- Organization URL Organziation website URL
- Technical Contact Name Name of the technical Person
- Technical Contact Email Email of the technical contact.
- Support Contact Name Name of the support contact person.
- Support Contact Email Email of the support contact person
- Signature Algorithm Algorithm that Ezeelogin would use on signing process
- Digest Algorithm Algorithm that Ezeelogin would use on digest process
- Service Provider Certificate X509 certificates for signing SAML requests
- Service Provider Key Private key for signing SAML requests.
- New Service Provider Certificate Key rollover. If you plan to update the Service Provider x509cert and privateKey you can define here the new x509cert and it will be published on the Service Provider metadata so that Identity Providers can read them and get ready for rollover.
- Allow Internal Authentication If enabled, then Ezeelogin will allow users to authenticate from internal database as well via a different URL.