How to Harden SSH Server?
Introduction
SSH Hardening Steps
1. Passwordless Authentication for SSH
By default, SSH requires a password to login in. By attempting the brute force attack and/or using the hacking tools, the hackers can crack the password and gain access to the server.
To overcome the attacks, the password-based authentication mechanism should be disabled.
- Login to the server and then open the sshd_config file,
vi /etc/ssh/sshd_config
2. Search for the directive: PasswordAuthentication, uncomment and change the value from yes to no
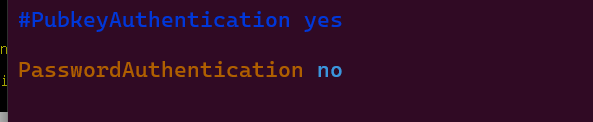
3. Save and close the file and then restart the SSH service.
systemctl restart sshd
Hackers must be aware of the username in order to log in to the remote server using SSH. All the Linux operating systems come with a root user by default. Hence it is not a good practice to allow root users for SSH authentication. We can create another user with the required privileges for SSH and disable root user login. By doing so, It will be tricky for the hackers to figure out the username to perform the brute force attacks.
- SSH to the Linux server or the bastion server and edit the sshd_config file.
- Find the directive: PermitRootLogin and change the value from yes to no.

3. Save the changes and then restart the SSH service.
By default, the SSH listens on port 22 which is widely known among hackers. Using the security tools, they can perform scanning on port 22 and perform brute force attacks. To avoid this, we have to use the custom port number for SSH authentication.
- Edit the ssh config file,
vi /etc/ssh/sshd_config
4. Uncomment the directive: Port and change the port from 22 to any random port you prefer.
3. Make sure to restart the SSH service
SSH connection should not be kept idle for a long time due to security reasons. Hence we should set idle timeout connections for SSH so that the connection gets closed when it reaches the idle timeout value. Idle connection timeout is disabled by default. Hence we have to set the idle connection timeout to 300 seconds.
1. To enable it, Edit the sshd_config file.
2. Uncomment the directive: ClientAliveInterval
3. And change the value from 0 to 300
4. Save and close the file.
5. Restart the SSH service for the changes to be effective.
Enabling a two-factor authentication mechanism for SSH takes security to the next level. During SSH, You will be asked to enter the 6 digit security code which you have received on the Authenticator app. First, the Google PAM module should be installed using the below commands,
To install on the Ubuntu operating systems,
apt-get install libpam-google-authenticator
To install on the RHEL / CentOs,
yum install google-authenticator qrencode-libs
The next step is to generate secret keys using the google authenticator pam mobile which was installed.
You can generate the secret keys by running the following command.
google-authenticator
Which asks for a few questions, answer the questions with yes.
The next step is to enable Google PAM authentication.
- For that, you need to edit the /etc/pam.d/sshd file and append the below line at the end of the file.
auth required pam_google_authenticator.so
2. Save and close the file.
And also we have to configure the SSH daemon to accept google authentication.
3. Open /etc/ssh/sshd_config file and then change the value for the directive: ChallengeResponseAuthentication to yes.

4. Save & close the file.
5. Restart the SSH service for the changes to take effect.
systemctl restart sshd
Fail2ban is an intrusion prevention software using which we can prevent SSH Brute force attacks. It checks the SSH failed login attempts from different IP sources, whenever these IP addresses cross certain failure attempts, fail2ban automatically blocks the SSH access for a specific period of time. By default, the IP address will be blocked for 10 minutes only. In order to avoid a brute force attack after 10 minutes, we can permanently block the IP addresses using the below configuration.
bantime = -1
Fail2ban can be installed using the below commands depending on the operating systems used.
apt-get install fail2ban -y
yum install fail2ban -y
TCP wrappers is a host-based networking ACL system using which we can filter incoming network traffic.
TCP wrappers works using two files:
/etc/hosts.allow
/etc/hosts.deny
- To deny all the incoming requests from all unknown hosts,
- Open the /etc/hosts.deny file and add the below configuration.
sshd : 192.168.10.5/32
To allow access from the specific IP address such as Office’s static public IP address and/or VPN server’s IP address
Open the /etc/hosts.allow and add the below configuration
sshd : 103.91.17.199/32
Replace 103.91.17.199 with the real public IP address. By doing so, incoming connection traffic will be accepted only from the allowed IP addresses.
To add an additional layer of security, we can allow only certain users who can remotely access the system and execute the commands.
- Open the config file , /etc/ssh/sshd_config
- Append the AllowUsers directive followed by user names as shown below.
AllowUsers robinson samuel
3. Once added, Save and close the file.
4. Restart the SSH for the changes to take effect using the below command.
systemctl restart sshd
As the key-based authentication is more secure and is very less prone to brute force attacks, We will configure SSH to accept only SSH public key authentication and completely disable password-based authentication.
- Edit the sshd_config file
2. Look for the directive: PubkeyAuthentication, Uncomment, and set the value to yes.
3. And also find the directive: PasswordAuthentication, Uncomment, and set the value to no

4. Save the changes and close the file.
Conclusion
We have learned to harden/secure the SSH server.
Following the above best practices will help us to prevent SSH attacks on the Linux servers, Jump server or bastion server.






