Trusted by enterprises across the globe..
Ezeelogin SSH Gateway
The ssh gateway software comes with tons of security features and automations which would help you manage and administrate hundreds of Linux servers .
A SSH Jump Server solution to secure ssh access of your employees to Linux servers/ devices, Routers , Switches , Cloud instances & to meet security compliances. It acts as a centralized SSH login server.
Why do you need a SSH Jump Server?
Centralize & Streamline ssh user logins
Securely manage and administer ssh user logins to Linux servers, Routers, Switches & Cloud instances easily and meet security compliances (PCI DSS, ISO 27001 & more) quickly.
Role Based Access Control ( RBAC ), PAM & IAM
Active Directory, LDAP, SAML Authentication supported
Manage employee access, identity and priviliege escalations on remote linux servers. This is a useful for meeting security compliances such as PCI DSS, ISO 27001 and much more.

used in Ezeelogin
Security is of paramount importance. Latest encryption technologies such as sha256, SHA256, BLOWFISH or DES, AES have been used to ensure that the ssh jumphost is indeed a unbreakable fortress.
MANAGE SERVER INFRASTRUCTURE EASILY.
The tool is an indispensable swiss knife for a system administrator. With its features and automation, one can now easily manage huge server infrastructure at the fraction of the time that was needed before.
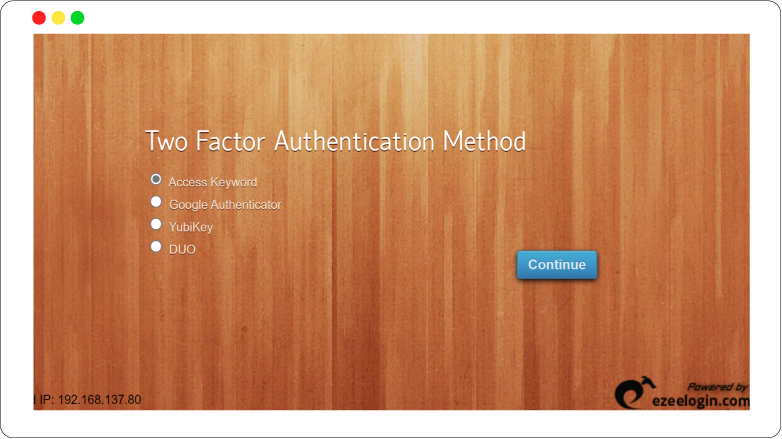
Google Authenticator, Yubikey, DUO Security supported
The ssh interface and the gui is now fortified with multi factor authentication mechanism such as Google Authenticator, Yubikey and DUO Security to ensure that ssh access to your Linux servers, instances, routers, switches are bullet proof. This helps in meeting compliance like PCI, ISO 27001 and more.
Command Line Interface ( CLI ) for fast SSH access
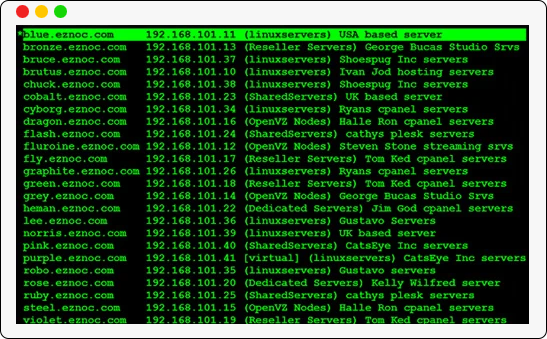
The jump host has an intuitive ssh interface that let you quickly navigate to remote hosts that a user has access to. Search for the remote hosts based on their hostname, ip address or other tags assigned to it.
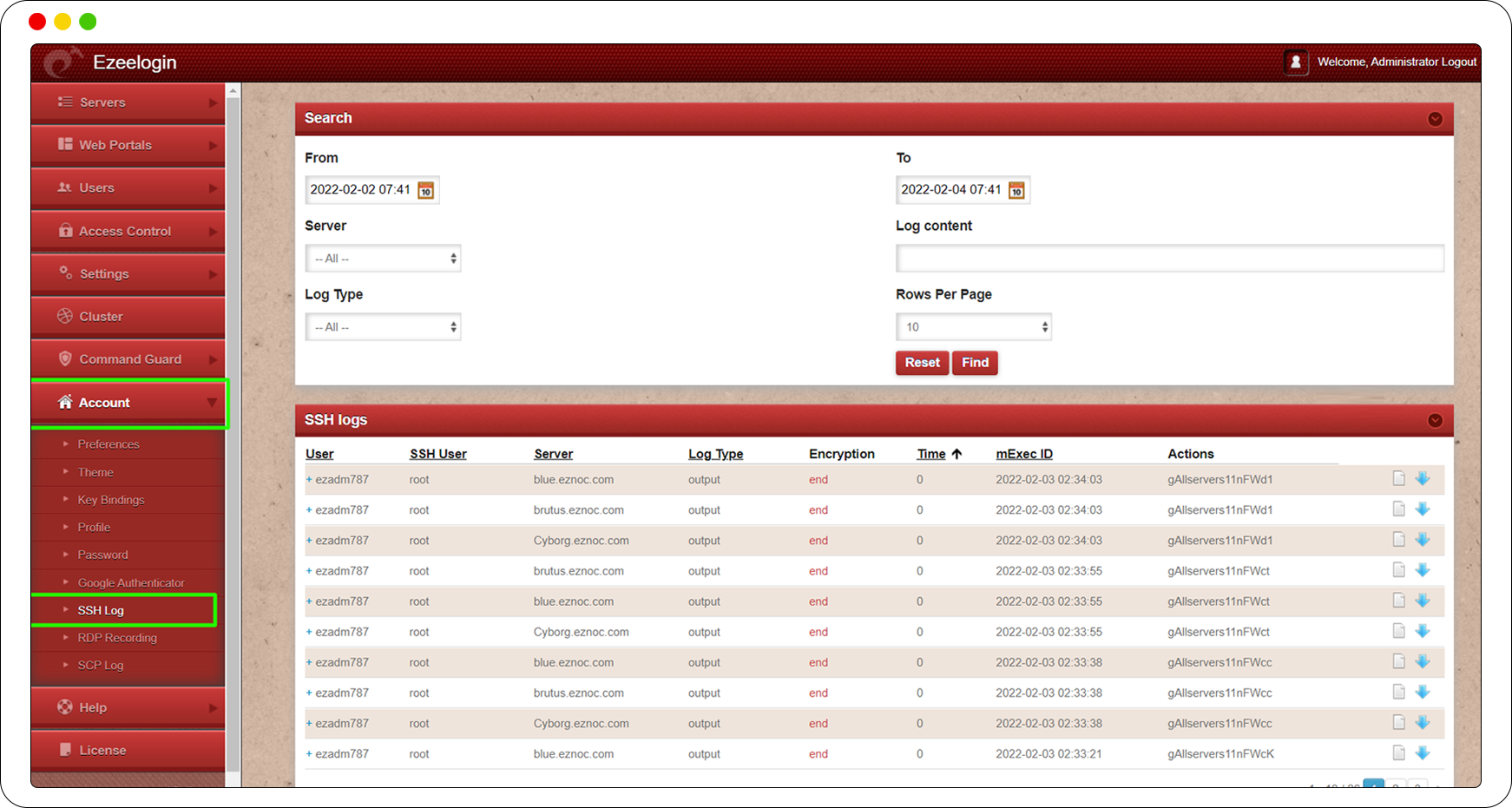
Record SSH Sessions
Record Employee activities in ssh
Record the ssh session of users accessing remote servers via the jump server. Watch what the ssh user does in real time. This is helpful for forensics audit and for meeting various compliance such as PCI DSS.
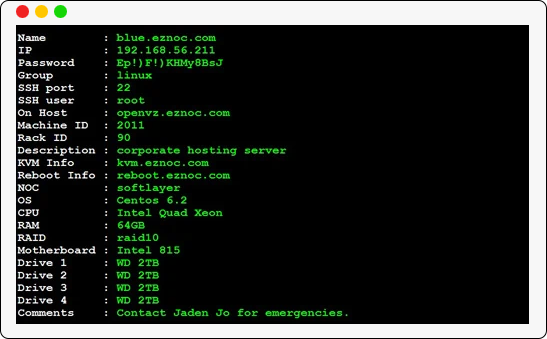
Access server details such as ip, ssh port number, password, hardware information such as cpu, ram, motherboard, hardrive, raid , rack id, data center details, kvm information with a single key press.