Just-in-time (JIT) access is a modern security practice which reduces risk by granting users privileges only when it is required and for a specific period, eliminating permanent access found in legacy access control models.
With JIT, users don’t carry admin or privileged roles all day. Instead, they request access, get approvals, complete the task, and then access automatically expires. There’s no need to manually revoke permissions or audit every role continuously.
Just-In-Time Access (JIT) significantly lowers identity threats, enforces least-privilege at scale, and aligns with zero-standing access principles where elevated rights must always be requested and justified. Whether protecting sensitive cloud infrastructure, securing business-critical applications, or preventing over-provisioned environments, JIT provides granular control .
Why Standing Access Increases Risk?
Standing access creates long-term risk, even when it feels necessary. Privileged accounts often accumulate permissions over time. Admins forget to revoke access after projects end, roles get cloned without scrutiny, and soon users hold far more access than required.
Attackers notice. If credentials are phished or leaked, standing access provides an open path to sensitive systems. Lateral movement becomes easier, detection becomes harder, and nothing appears suspicious because the activity uses legitimate — but excessive — privileges.
Standing access also weakens compliance and auditability. When permissions exist by default, it’s difficult to know who used them, when, and for what purpose. This creates blind spots for security teams and pressure on incident response.
JIT flips this model. No one gets elevated access until they request it, and even then, it’s limited, tracked, and enforced. Access exists only for a purpose, and only for a set time.
How Just-in-Time (JIT) Access Works?
Just-In-Time Access (JIT) replaces persistent privileges with time-bound, purpose-driven access. Instead of handing out permanent permissions, organizations approve temporary access that automatically closes when the task is complete.
Some companies use fully automated on-demand access tied to criteria like user role or risk score. Others require a human approval step for sensitive systems or administrative tasks. In both cases, the principle remains: no one keeps elevated access by default.
Just-in-Time (JIT) Access Workflow
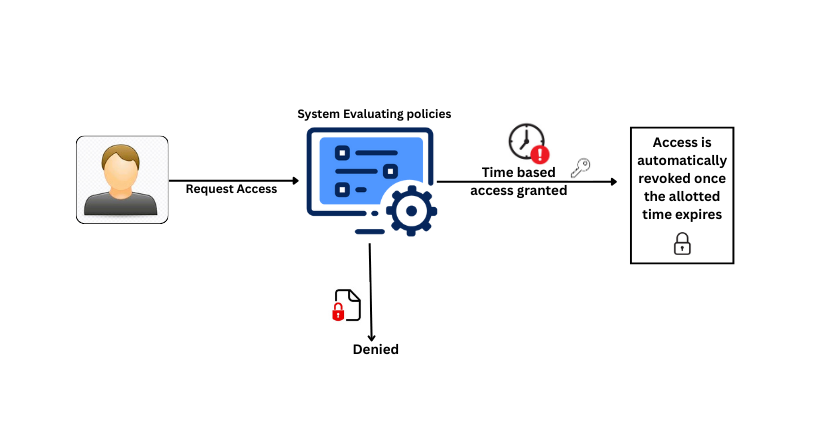
The workflow typically looks like this:
- User requests access via a ticket, portal, or workflow.
- System evaluates policies and grants or denies access.
- If approved, permissions are assigned for a fixed duration (often hours).
- Once the time expires, access is revoked automatically.
- Every session is logged for auditability.
Just-In-Time Access (JIT) integrates with identity providers, cloud platforms, and infrastructure tools, enabling least privilege without slowing developers, engineers, or external partners.
JIT and Privileged Access Management (PAM)
Privileged access management (PAM) limits who can access high-value systems. But traditional PAM often relies on persistent or oversized privileges.
JIT enhances PAM by removing those standing permissions and replacing them with temporary, auditable access. Instead of broad, always-on rights, users gain just enough access for just enough time.
This:
- Shrinks the attack surface.
- Improves audit trails (who accessed what, when, and for how long).
- Eliminates cleanup tasks since access expires automatically.
Key Use Cases for JIT Access
JIT is not just a theoretical control. It solves real-world problems across industries:
- Financial Services → Secure client data with multi-approver workflows and short access windows for encrypted cloud resources.
- Engineering & Manufacturing → Manage multi-cloud environments by reducing excessive privileges and preventing lateral movement.
- SaaS Applications → Limit data exposure by granting business users temporary access only when needed.
- DevOps & Engineering → Allow fast troubleshooting and deployments with temporary elevated rights that auto-revoke.
- Third-Party Vendors → Grant contractors or partners access only for a fixed window tied to a ticket or schedule.
Across these scenarios, Just-In-Time Access (JIT )reduces identity misuse risk while supporting productivity.
JIT and Zero Standing Access
Zero Standing Access (ZSA) means no one has permanent elevated privileges. With JIT, users request access when needed, gain it temporarily, and lose it automatically.
This eliminates dependency on manual cleanup and enforces least privilege by design. Every elevation is logged, every session has an expiration, and no persistent backdoors remain for attackers.
Evaluating JIT Access Tools
When choosing a JIT solution, look for:
- Visibility → Who is requesting access, what roles they need, and how they use them.
- Policy Controls → Automated workflows, approval steps, role-based conditions, and flexible expiration.
- Integration → Support for identity systems, cloud platforms, and hybrid environments.
- Automation → Enforced expiration, approvals, revocations, and audit logs with minimal manual work.
A strong JIT platform adapts to workflows, scales across environments, and reduces operational burden.
Best Practices for Implementing JIT
- Define who can request access, what they can access, and under what conditions.
- Require purpose justification and log every session.
- Apply short expiration windows by default; force re-requests when needed.
- Automate enforcement, approvals, and revocations.
- Connect JIT events to exposure management and vulnerability management platforms for stronger risk-based controls.
- Test policies regularly to ensure expiration, logging, and workflows work as intended.
FAQs
1. What is JIT PAM?
JIT PAM means the Time-limited privileged access that replaces standing permissions.
2. How does Just-In-Time Access (JIT) differ from standing access?
Standing = permanent.
JIT = temporary and controlled.
3. Which tools support JIT?
Identity providers, PAM solutions, cloud-native tools, and exposure management platforms.
JIT and the Future of Privilege Control
Just-in-time access offers a smarter, faster way to manage privilege. JIT granting privilege only when required and only for a specific period, organizations reduce identity risk and shrink the window of opportunity for attackers.
With platforms support JIT, becomes risk-aware, auditable, and scalable across multi-cloud environments. You can:
- Reduce excessive access in cloud roles and IAM groups.
- Eliminate audit gaps caused by static permissions.
- Enforce consistent controls across cloud platforms and on-premises.
- Protect overexposed admin accounts in DevOps, vendor, and emergency workflows.
By adopting Just-In-Time Access (JIT), you not only secure privileged identities but also accelerate your journey toward least privilege, zero standing access, and zero trust security.







