How do I configure Ezeelogin to authenticate using OpenLdap(Pam-Ldap) in CentOS ?
Integration of Open-LDAP (PAM-LDAP) in CentOS
Overview: This article details how to integrate OpenLDAP (PAM-LDAP) with CentOS for SSH authentication using Ezeelogin. It covers installing PHP-LDAP, configuring LDAP settings via the web GUI, and setting up PAM_LDAP for SSH access. Verification steps ensure imported LDAP users are correctly configured for seamless integration.
Make sure that the PHP-LDAP extension is installed on the server.
root@gateway:~# yum install php-ldap openldap openldap-clients ;apachectl restart
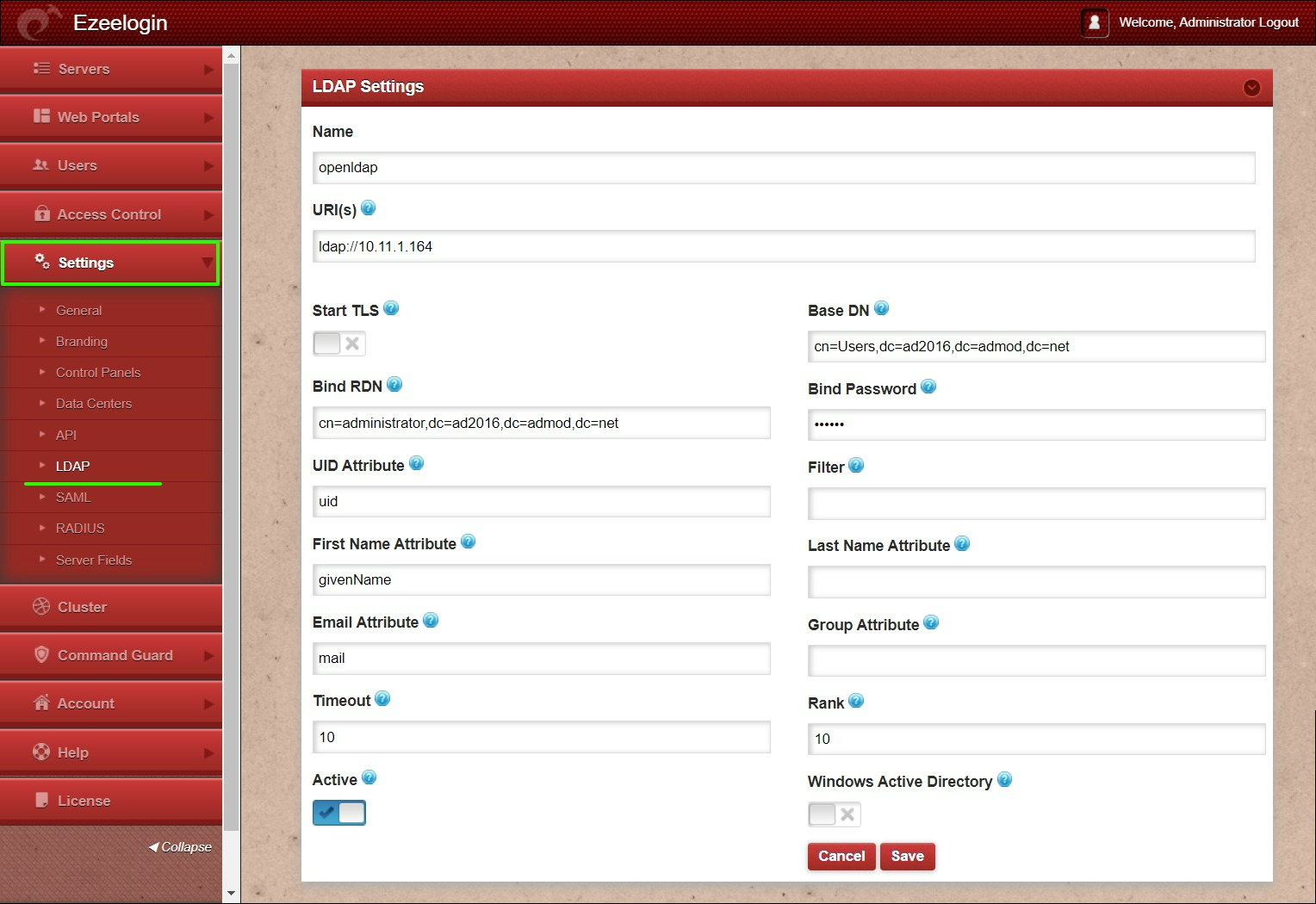
Step 1: Login to Web-GUI -> Settings -> LDAP
Add the details of LDAP configurations
Multiple URIs or a list of URIs can be specified in the format:
- ldaps://host.com:636/ ldaps://host.com:636/
(Only the protocol, hostname, and port fields are allowed.)
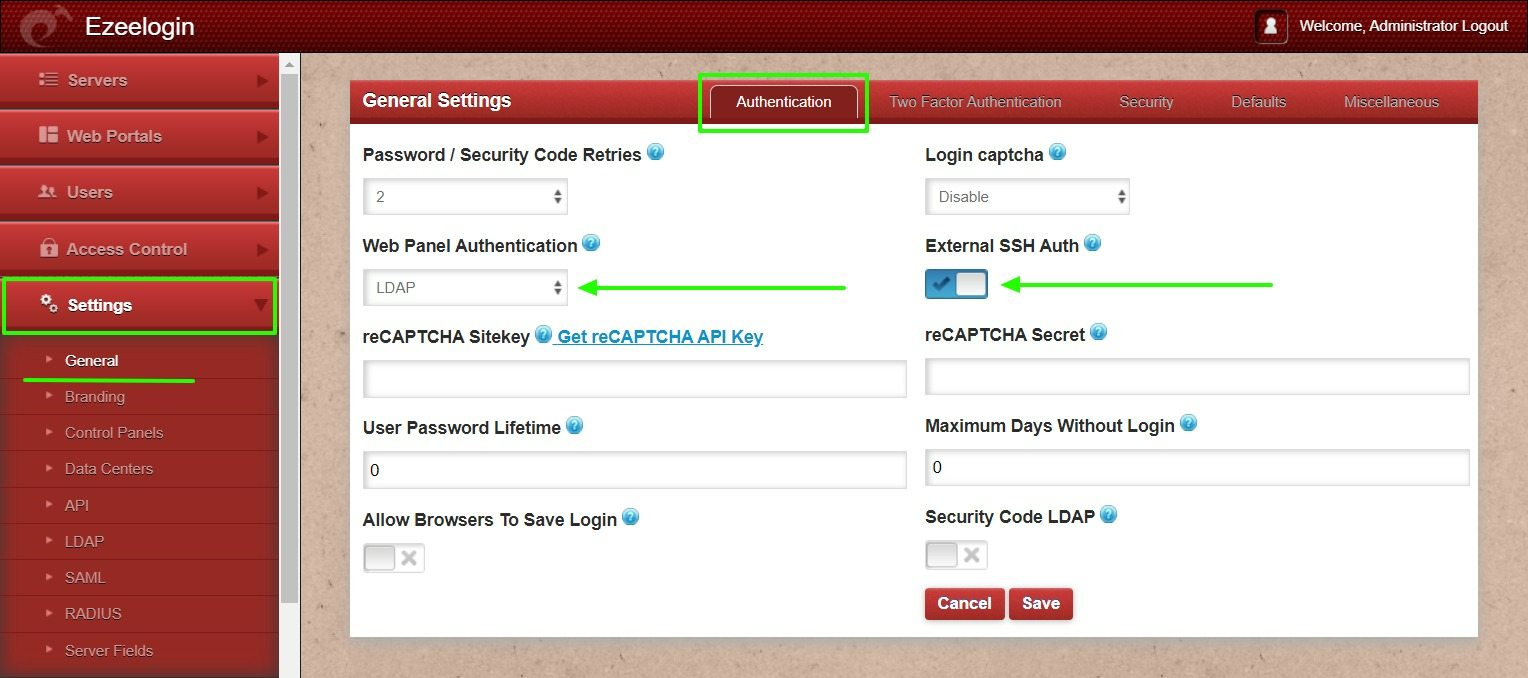
Step 2: Under Settings -> General -> Authentication -> change web panel authentication to LDAP & Enable External SSH Auth
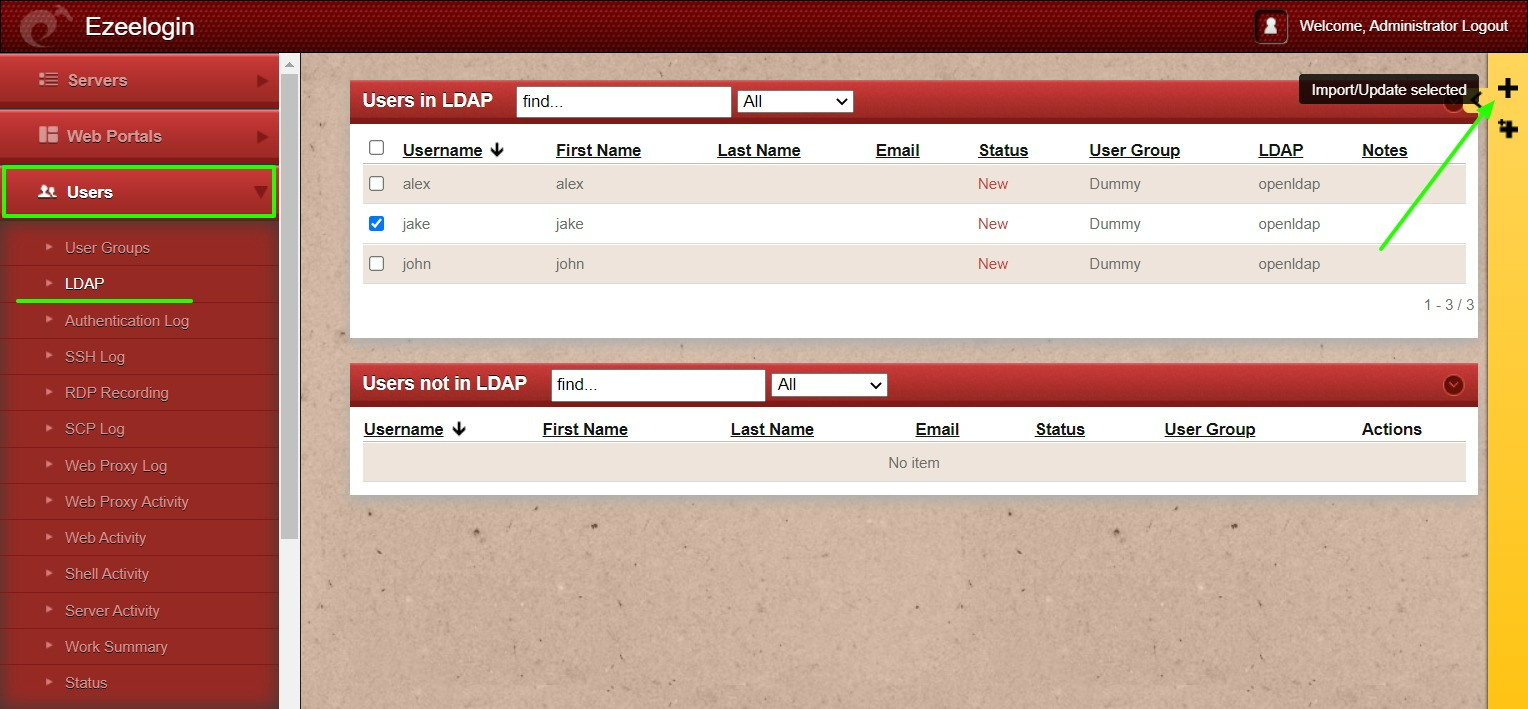
Note: After importing the users to Ezeelogin, log in with the user and set up the security code for the user under Account -> Password -> New Security Code.
Let's configure PAM_LDAP Authentication for SSH
root@gateway:~# yum install nss-pam-ldapd nscd
root@gateway:~# authconfig-tui
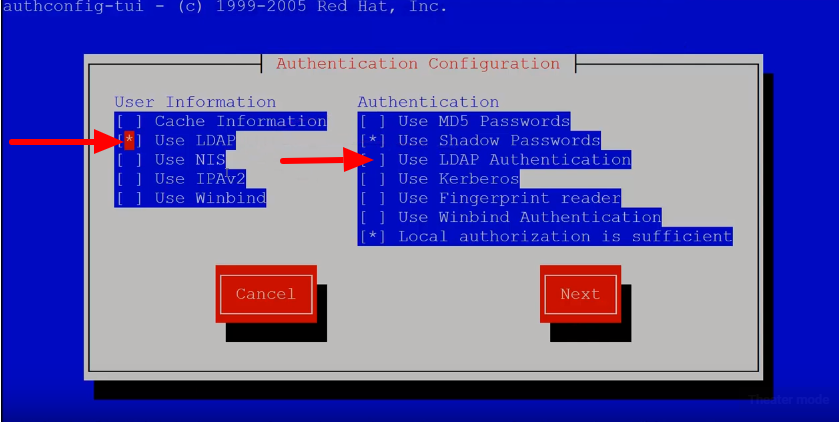
root@gateway:~# vi /etc/nslcd.conf
binddn cn=admin,dc=eztest,dc=net
bindpw chaSD@#234JH56hj^7
map passwd loginShell "/usr/local/bin/ezsh"
root@gateway:~# authconfig --enablemkhomedir --update
root@gateway:~# service nslcd restart && service nscd restart
Note:
Ensure the login shell of the LDAP user is /usr/local/bin/ezsh
root@gateway:~# finger jake
Login: jake Name: jake t
Directory: /home/jake Shell: /usr/local/bin/ezsh
Last login Wed Jun 13 05:02 (EDT) on pts/1 from 10.1.1.13
No mail.
No Plan.
root@gateway:~# id jake
uid=1001(jake) gid=20001(domain users) groups=1547600513(domain users)
root@gateway:~# ldapsearch -v -x -H ldap://10.11.1.164 -b "cn=jake j,cn=Users,dc=ad2016,dc=admod,dc=net" -D "cn=administrator,dc=ad2016,dc=admod,dc=net" -w redhat
ldap_initialize( ldap://10.11.1.103:389/??base )
filter: (objectclass=*)
requesting: All userApplication attributes
# extended LDIF
#
# LDAPv3
# base <cn=jake j,dc=ad2016,dc=admod,dc=net> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# jake j, ad2016.admod.net
dn: cn=jake j,dc=ad2016,dc=admod,dc=net
cn: jake j
givenName: jake
gidNumber: 500
sn: j
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
userPassword:: e01ENX15VHpOZUxJSFpTZzBZaGF6c3ZjQjVnPT0=
uidNumber: 1001
uid: jake
homeDirectory: /home/jake
loginShell: /usr/local/bin/ezsh
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
Quotation content