Integrate Windows AD on RHEL 8 using SSSD
How can I integrate Windows AD on RHEL 8 using SSSD?
Overview: This article provides a step-by-step guide to integrating Windows Active Directory (AD) with RHEL 8 using SSSD, covering package installation, domain configuration, user verification, and enabling AD authentication in Ezeelogin.
Note:
1. Ensure that the following ports on the RHEL host are open and accessible to the AD domain controllers.
DNS =53, LDAP =389, Kerberos 88 & 464, LDAP Global Catalog 3268,LDAPS 636 and NTP 123 (UDP)
2. Verify that the system time on both systems is synchronized. This ensures that Kerberos is able to work correctly.
Refer to the article: correct server time in Centos, RHEL, Ubuntu, SUSE
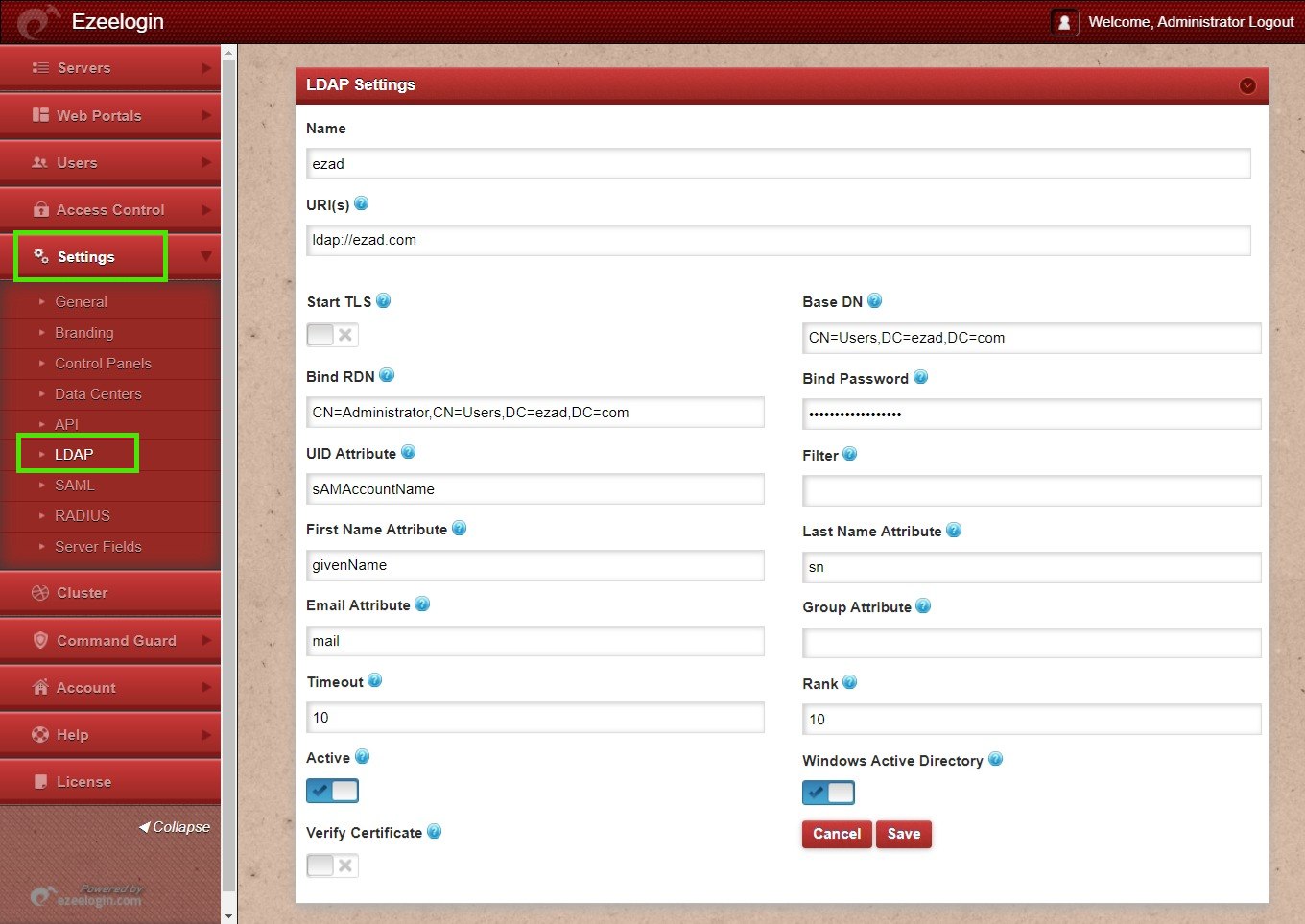
Step 1. Login to Ezeelogin Web-GUI -> open settings -> Ldap. Refer the article How to find base DN and bind RDN
Multiple URIs or a list of URIs can be specified in the format:
- ldaps://host.com:636/ ldaps://host.com:636/
(Only the protocol, hostname, and port fields are allowed.)
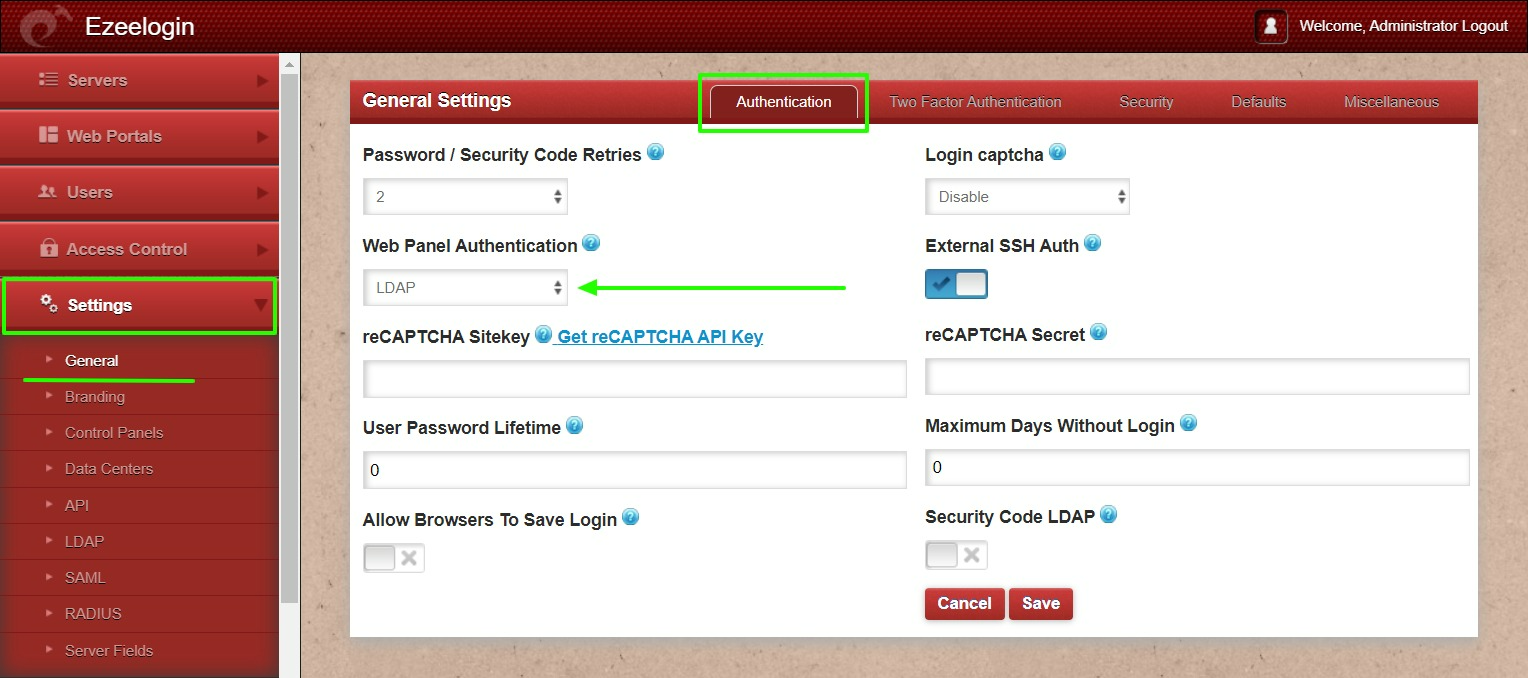
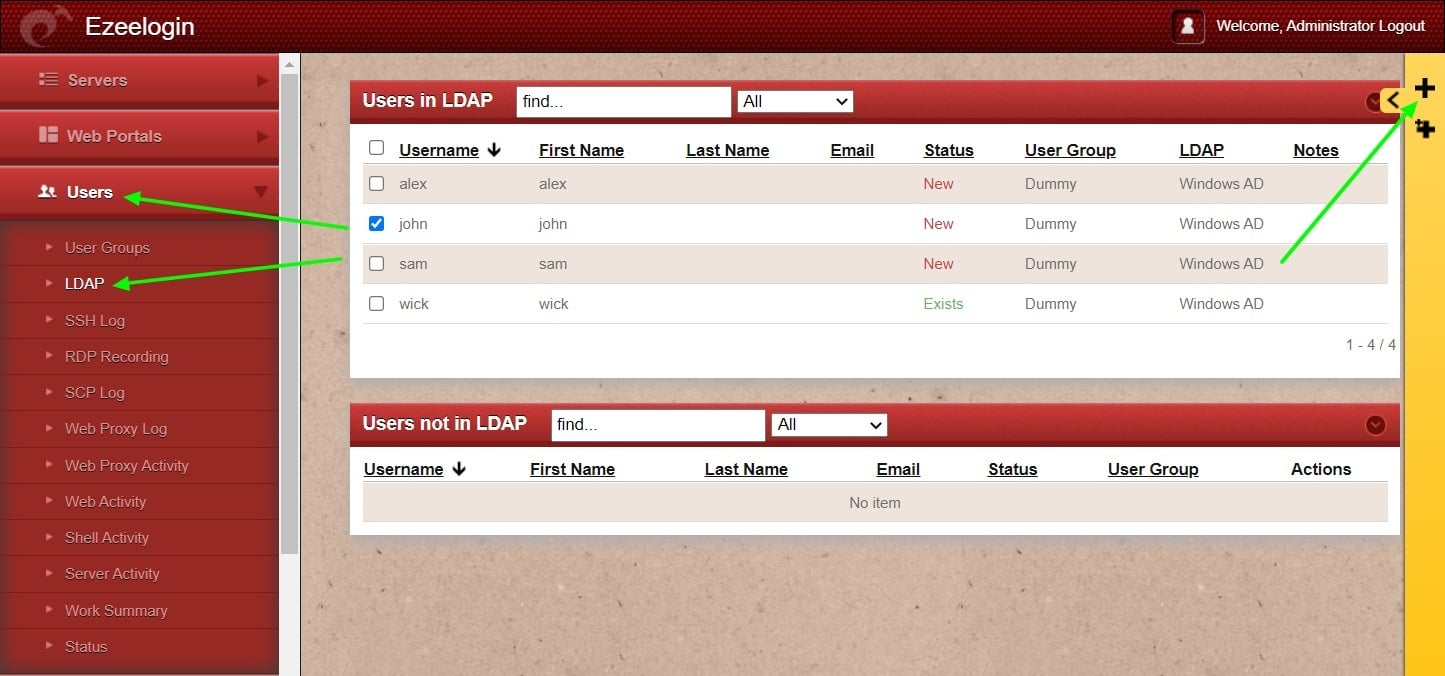
You can confirm the imported LDAP users were listed in the Users tab in Ezeelogin GUI. You will be able to log in to Ezeelogin GUI with windows user credentials.

Backend configuration to integrate Windows with RHEL 8
yum install samba-common-tools realmd oddjob oddjob-mkhomedir sssd adcli krb5-workstation nscd
Note: Ensure that you are using the AD domain controller server for DNS.
Step 3. Add in windows server IP /etc/resolv.conf to resolve and disc over AD do main.
Step 4. To display information for a specific domain, run realm discover and add the name of the domain you want to discover.
realm discover ezad.com
ezad.com
type: kerberos
realm-name: EZAD.COM
domain-name: ezad.com
configured: no
server-software: active-directory
client-software: sssd
required-package: oddjob
required-package: oddjob-mkhomedir
required-package: sssd
required-package: adcli
required-package: samba-common-tools
getent passwd administrator@ezad.com
administrator@ezad.com:*:644600500:644600513:Administrator:/home/administrator@ezad.com:/bin/bash
Step 7. After successful join, edit /etc/sssd/sssd.conf and change use_fully_qualified_names to False and append the following override_shell
=/usr/local/bin/ezsh
Step 8. Restart sssd and nscd using the below commands.
Step 9. Run id username /getent passwd username and s ee AD user de tails.
Note: Verify Certificate feature is only available from Ezeelogin version 7.35.0.