LDAP Filters for Active Directory Users
How to add LDAP Filters for Active Directory Users in Ezeelogin
Overview: This article explains how to use LDAP filters in Ezeelogin to manage users based on their group memberships in Active Directory (AD). The examples are built using AD structure with the groups windows AD and Developers AD.
Example Environment details:
Base DN: OU=develop,DC=ezldap,DC=com
All users are stored inside this Organizational Unit (OU).
Groups in this OU:
1.windows AD
DN: CN=windows AD,OU=develop,DC=ezldap,DC=com
Example member: CN=Joy,OU=develop,DC=ezldap,DC=com
2.Developers AD
DN: CN=Developers AD,OU=develop,DC=ezldap,DC=com
Understanding LDAP Filters: LDAP filters are queries that find users or other directory entries based on their attributes—like group membership.
Operators:
& (AND): Matches if all conditions are true
| (OR): Matches if at least one condition is true
! (NOT): Matches if the condition is false
Example 1: Find users in OU=develop who are in either "windows AD" OR "Developers AD"
Explanation: Finds users who belong to at least one of these two groups.
Use case:
All users who have access to a particular service or resource can be listed as follows.
LDAP Filter:
(|(memberOf=CN=windows AD,OU=develop,DC=ezldap,DC=com)(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com))
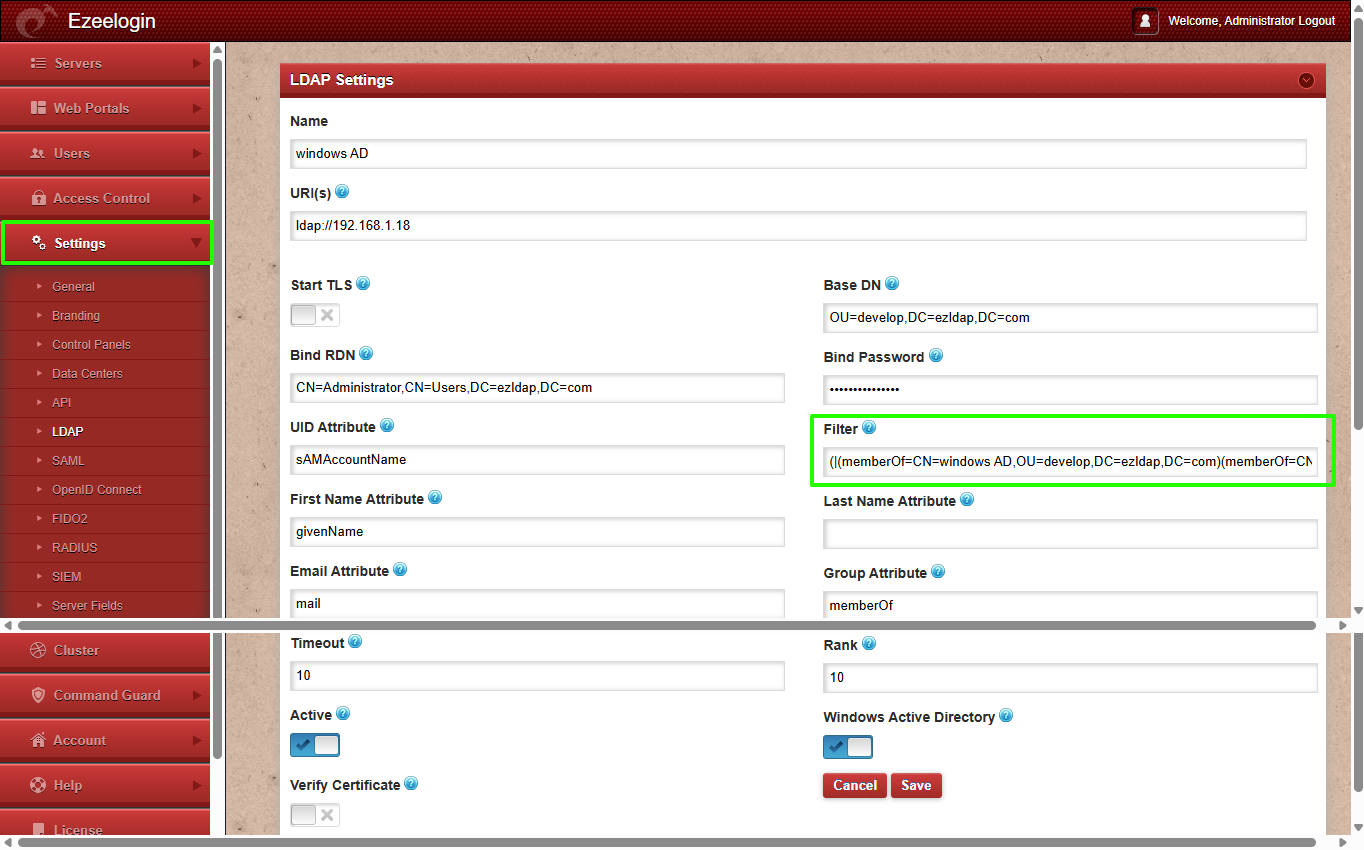
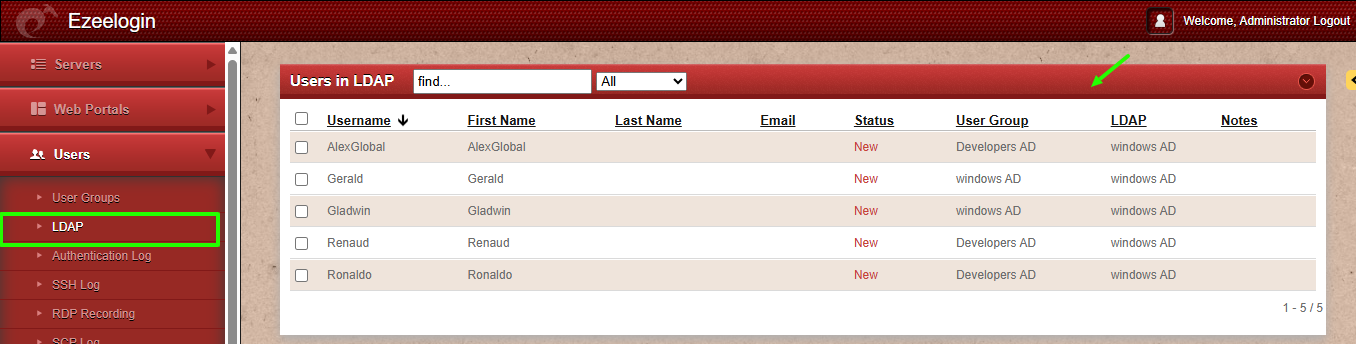
➡ Retrieves users in develop OU who are members of one or both groups.
Example 2: Find users in OU=develop who are in BOTH "windows AD" AND "Developers AD"
LDAP Filter:
(&(memberOf=CN=windows AD,OU=develop,DC=ezldap,DC=com)
(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com))
Explanation:
Finds users who are members of both groups at the same time.
Use case:
In cases where users require permissions in both systems.
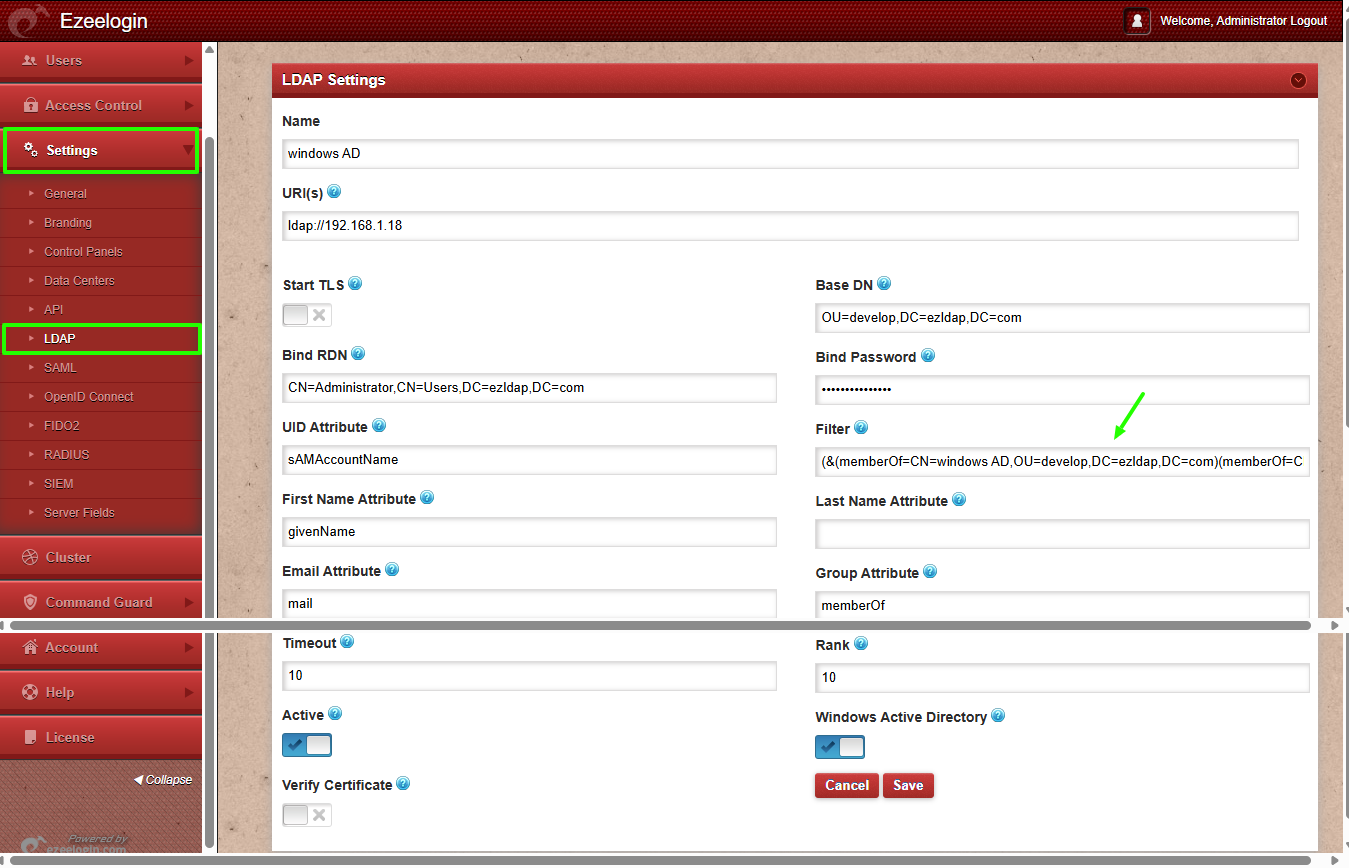
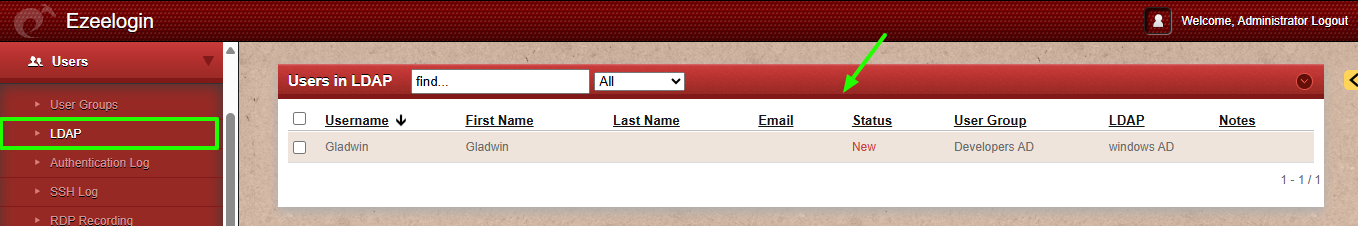 ➡ Retrieves users who are members of both groups.
➡ Retrieves users who are members of both groups.
Example 3: Find users in OU=develop who are NOT in "Developers AD"
LDAP Filter:
(!(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com))
Explanation:
Finds users who are in 'develop' but not part of 'Developers AD'.
Use case: If you want to exclude certain users from access or permissions.
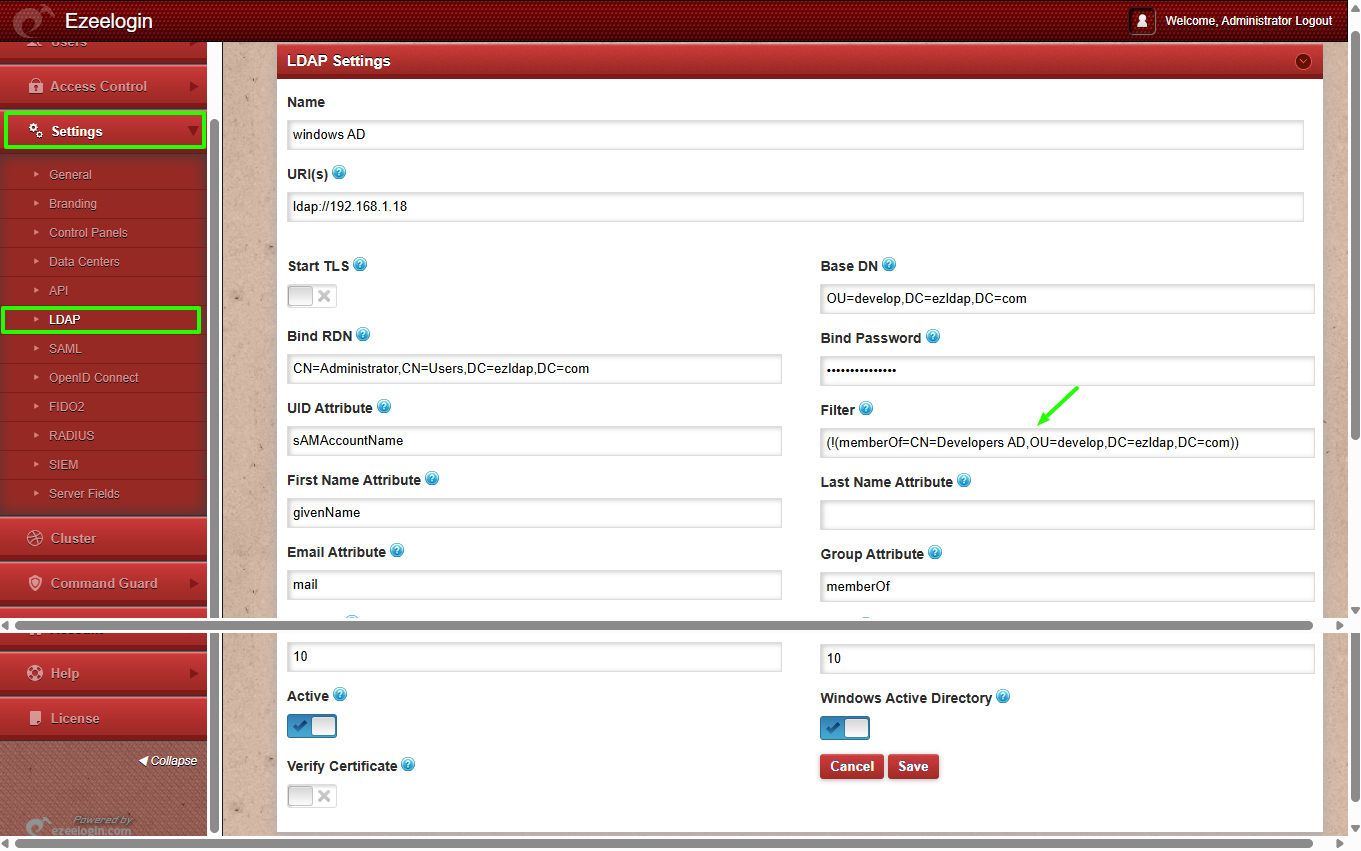
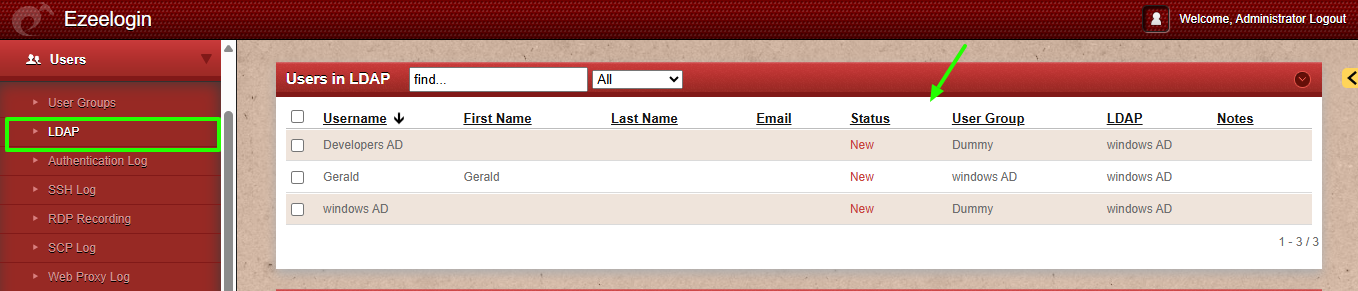 ➡ Retrieves users in develop OU that are not members of this group.
➡ Retrieves users in develop OU that are not members of this group.
Example 4: Find users in OU=develop who are in "windows AD" but NOT in "Developers AD"
LDAP Filter:
(&(memberOf=CN=windows AD,OU=develop,DC=ezldap,DC=com)(!(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com)))
Explanation:
Finds users who are in 'windows AD' but not part of 'Developers AD'.
Use case:
Access can be restricted to members of one group while explicitly excluding those who are also part of another group.
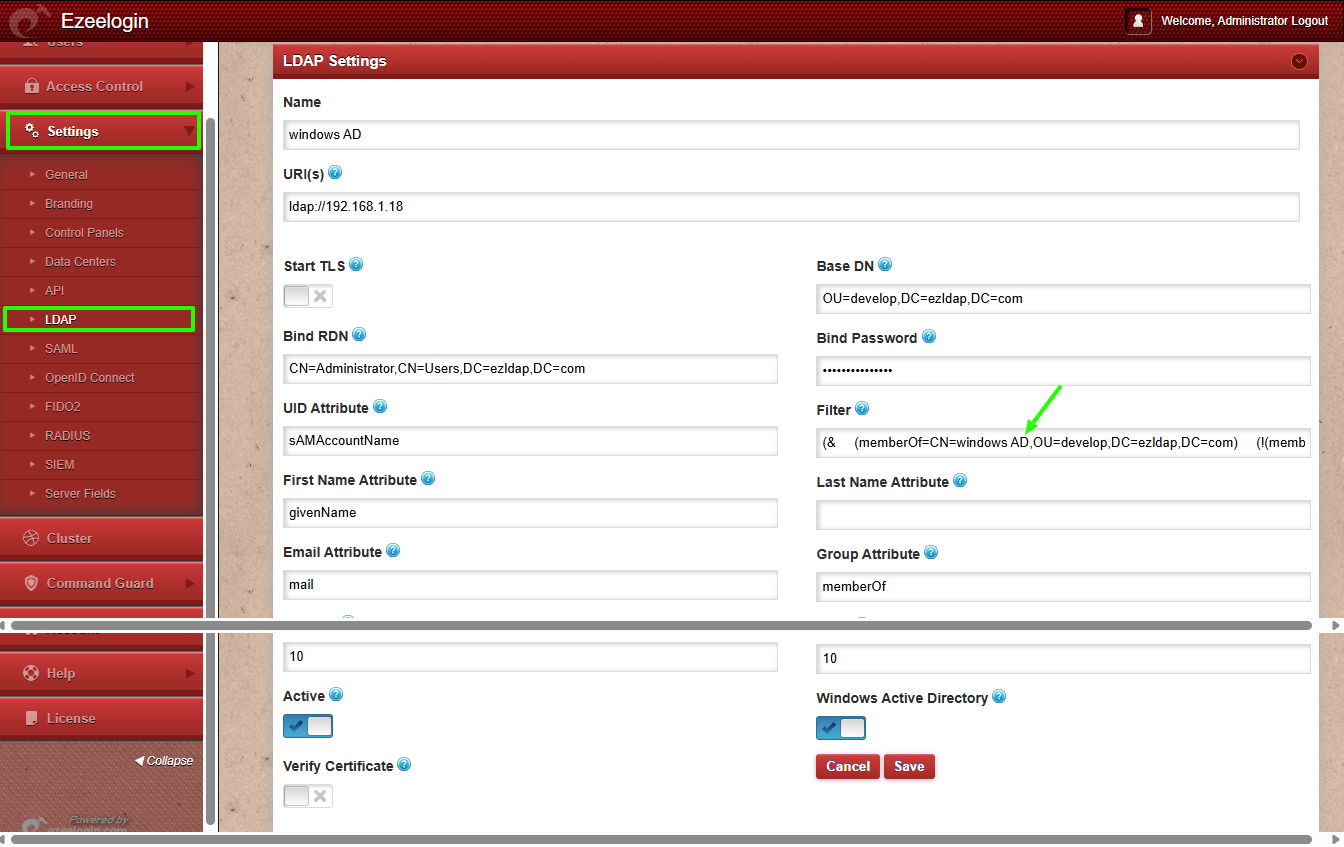
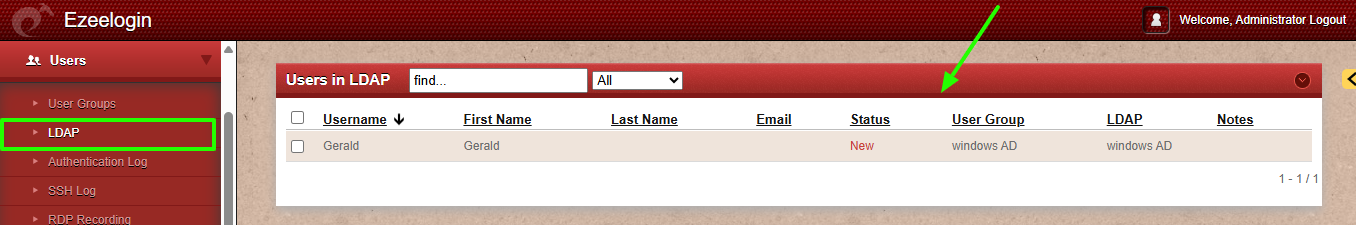
➡ Retrieves users in develop OU who are members of the first group and not in the second.
Applying the filters in Ezeelogin:
- Go to Users → LDAP in the Ezeelogin admin interface.
- Set Base DN as: OU=develop,DC=ezldap,DC=com
- Paste one of the filters in the LDAP Filter section.
- Save and click Test Connection.
- Check Users in LDAP to see the result.
- Import users as needed.
Key takeaways:
✔ Filter users based on group membership using &, |, and !.
✔ Use the full DN of the group inside memberOf.
✔ Filters can be combined for complex queries.
✔ Ezeelogin allows to view and manage users based on these LDAP filters in real-time.
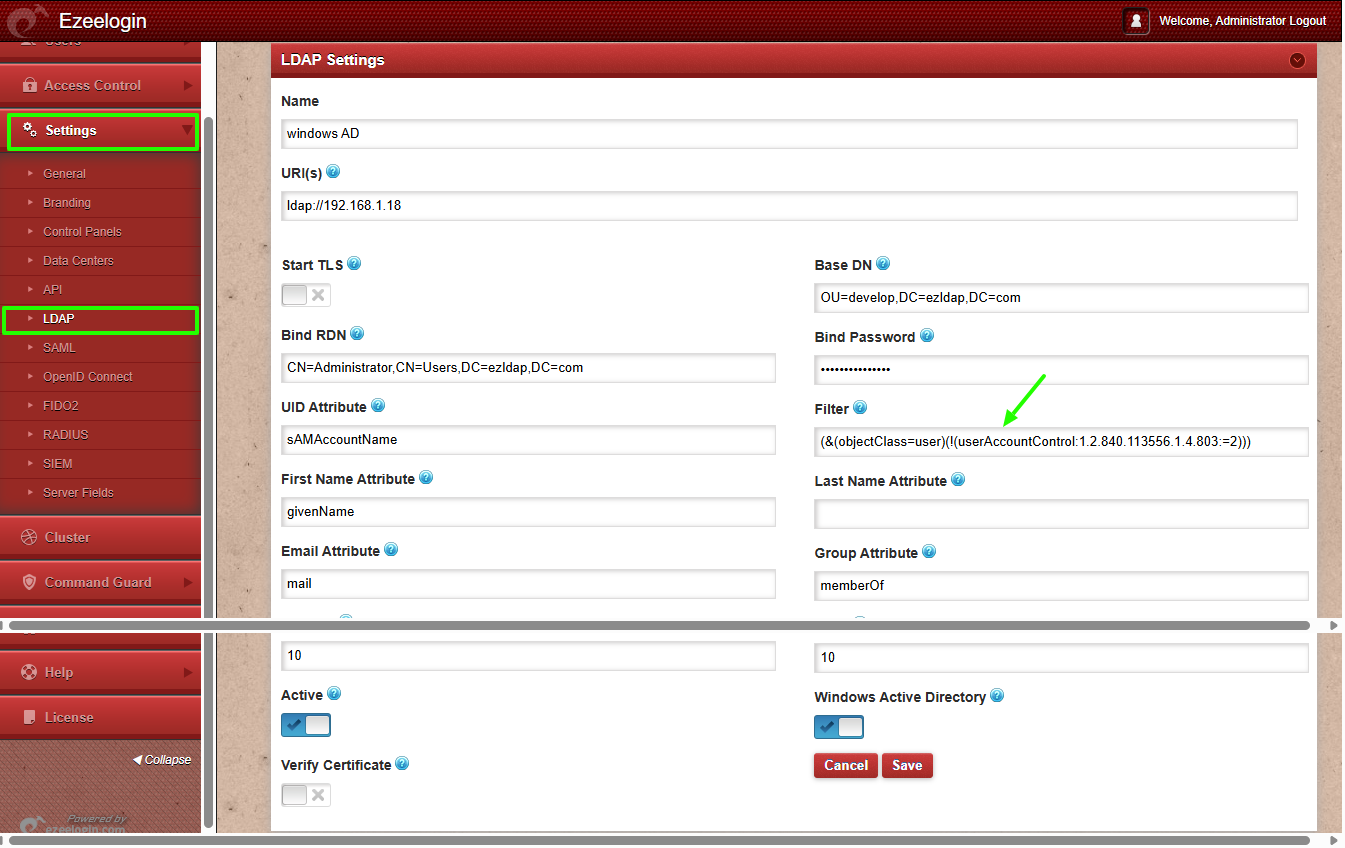
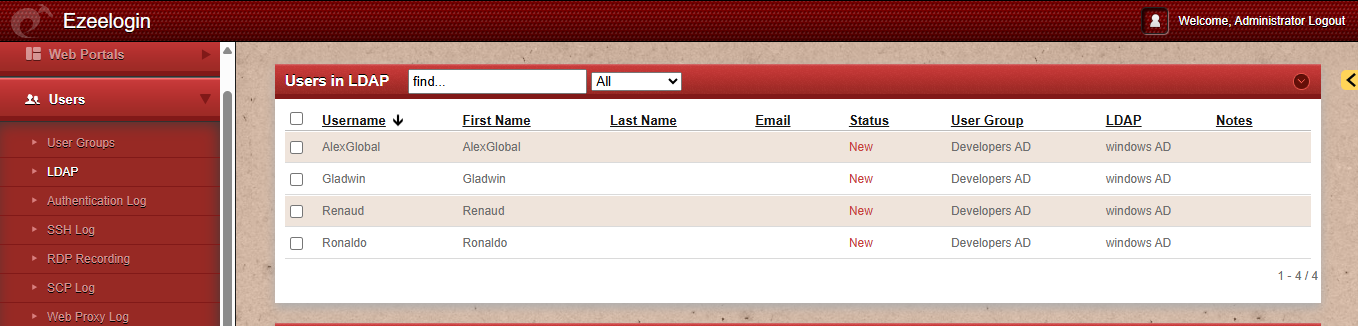
List Enabled User Accounts (LDAP filter for enabled accounts):
(&(objectClass=user)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))
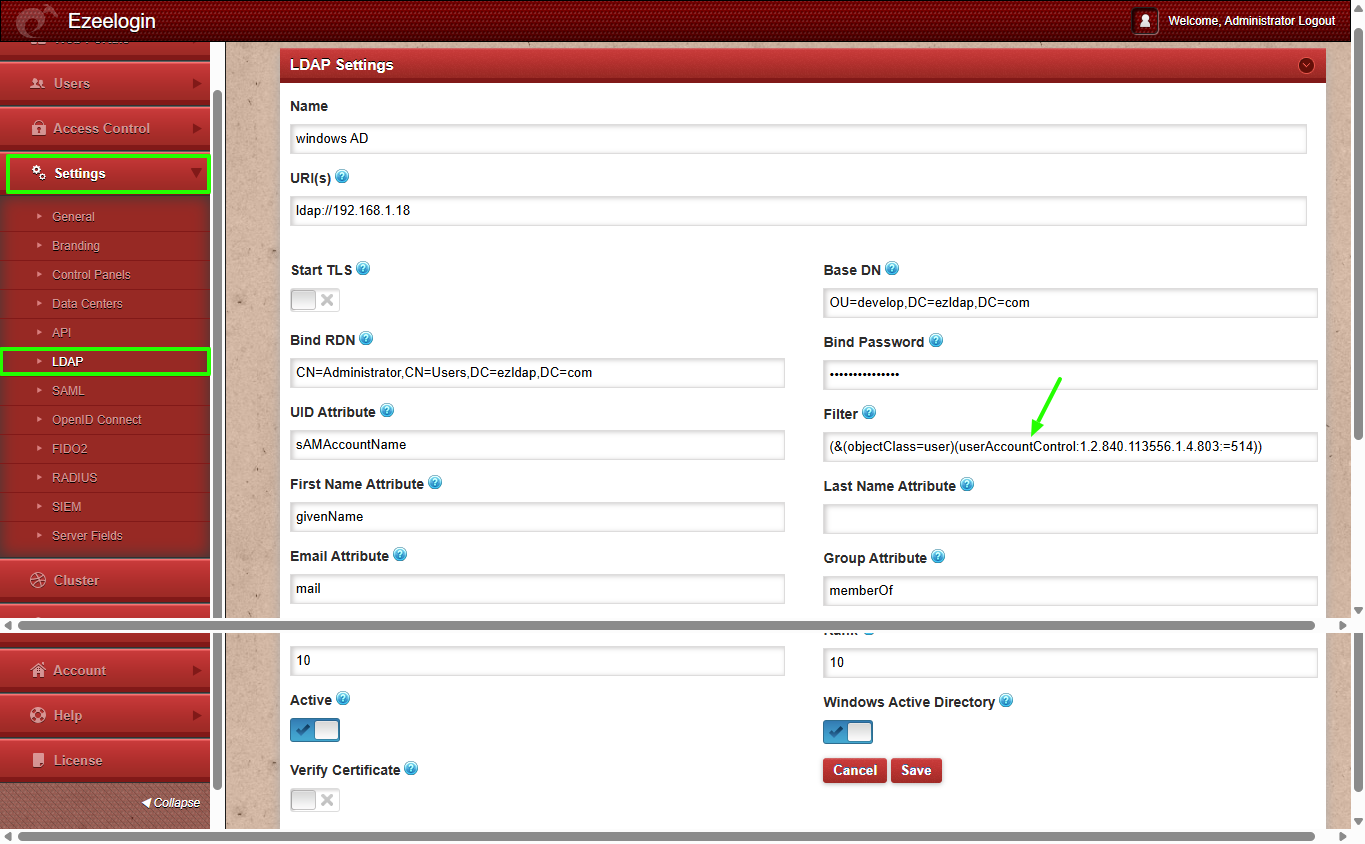
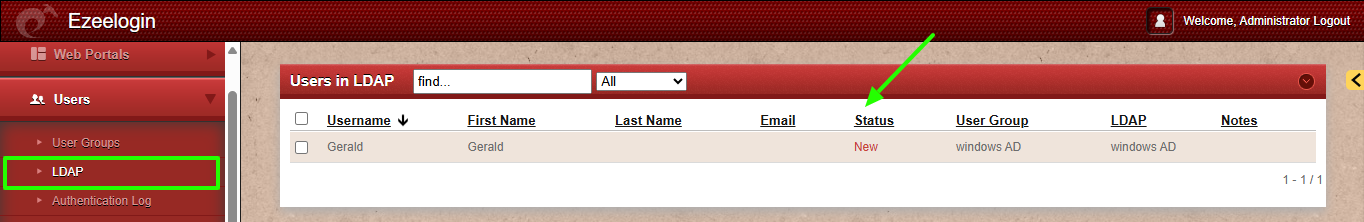
List Disabled accounts only:
Disabled accounts in AD have the userAccountControl flag 514.
(&(objectClass=user)(userAccountControl:1.2.840.113556.1.4.803:=514))
LDAP Search Command to List All Above Conditions of Filters
Example 1 — Users in "windows AD" OR "Developers AD"
root@gateway:~# ldapsearch -x -H ldap://192.168.1.18 -D "CN=Administrator,CN=Users,DC=ezldap,DC=com" -W -b "OU=develop,DC=ezldap,DC=com" "(|(memberOf=CN=windows AD,OU=develop,DC=ezldap,DC=com)(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com))"
The output of the above ldapsearch command is shown below.
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <OU=develop,DC=ezldap,DC=com> with scope subtree
# filter: (|(memberOf=CN=windows AD,OU=develop,DC=ezldap,DC=com)(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com))
# requesting: ALL
#
# AlexGlobal, develop, ezldap.com
dn: CN=AlexGlobal,OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: AlexGlobal
givenName: AlexGlobal
distinguishedName: CN=AlexGlobal,OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250924003755.0Z
whenChanged: 20250924003756.0Z
displayName: AlexGlobal
uSNCreated: 127036
memberOf: CN=Developers AD,OU=develop,DC=ezldap,DC=com
uSNChanged: 127041
name: AlexGlobal
objectGUID:: vZneTJfJJEmLyDEndhl9Lg==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 134031478759414308
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAytlsHZqhFKFfZ06wXgYAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: AlexGlobal
sAMAccountType: 805306368
userPrincipalName: AlexGlobal@ezldap.com
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=ezldap,DC=com
dSCorePropagationData: 20250924003756.0Z
dSCorePropagationData: 16010101000000.0Z
# Ronaldo, develop, ezldap.com
dn: CN=Ronaldo,OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Ronaldo
givenName: Ronaldo
distinguishedName: CN=Ronaldo,OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250924005855.0Z
whenChanged: 20250924005856.0Z
displayName: Ronaldo
uSNCreated: 127068
memberOf: CN=Developers AD,OU=develop,DC=ezldap,DC=com
uSNChanged: 127073
name: Ronaldo
objectGUID:: v7KY0XBGX0WNqMyWs7ExYw==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 134031491360247740
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAytlsHZqhFKFfZ06wYQYAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: Ronaldo
sAMAccountType: 805306368
userPrincipalName: Ronaldo@ezldap.com
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=ezldap,DC=com
dSCorePropagationData: 20250924005856.0Z
dSCorePropagationData: 16010101000000.0Z
# Renaud, develop, ezldap.com
dn: CN=Renaud,OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Renaud
givenName: Renaud
distinguishedName: CN=Renaud,OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250924011836.0Z
whenChanged: 20250924011837.0Z
displayName: Renaud
uSNCreated: 127591
memberOf: CN=Developers AD,OU=develop,DC=ezldap,DC=com
uSNChanged: 127596
name: Renaud
objectGUID:: IuctUG4GO0qngURhgAm0YA==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 134031503169520050
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAytlsHZqhFKFfZ06wYgYAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: Renaud
sAMAccountType: 805306368
userPrincipalName: Renaud@ezldap.com
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=ezldap,DC=com
dSCorePropagationData: 20250924011837.0Z
dSCorePropagationData: 16010101000000.0Z
# Gladwin, develop, ezldap.com
dn: CN=Gladwin,OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Gladwin
givenName: Gladwin
distinguishedName: CN=Gladwin,OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250924012727.0Z
whenChanged: 20250924012727.0Z
displayName: Gladwin
uSNCreated: 127613
memberOf: CN=windows AD,OU=develop,DC=ezldap,DC=com
memberOf: CN=Developers AD,OU=develop,DC=ezldap,DC=com
uSNChanged: 127621
name: Gladwin
objectGUID:: X6yQuoeC9EirR4np2gBYRA==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 134031508473159222
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAytlsHZqhFKFfZ06wZAYAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: Gladwin
sAMAccountType: 805306368
userPrincipalName: Gladwin@ezldap.com
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=ezldap,DC=com
dSCorePropagationData: 20250924012727.0Z
dSCorePropagationData: 16010101000000.0Z
# Gerald, develop, ezldap.com
dn: CN=Gerald,OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Gerald
givenName: Gerald
distinguishedName: CN=Gerald,OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250924012140.0Z
whenChanged: 20250924014130.0Z
displayName: Gerald
uSNCreated: 127602
memberOf: CN=windows AD,OU=develop,DC=ezldap,DC=com
uSNChanged: 127624
name: Gerald
objectGUID:: OqYP+V0xjkOpBb8x5M2eAw==
userAccountControl: 66050
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 134031505005918452
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAytlsHZqhFKFfZ06wYwYAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: Gerald
sAMAccountType: 805306368
userPrincipalName: Gerald@ezldap.com
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=ezldap,DC=com
dSCorePropagationData: 20250924012140.0Z
dSCorePropagationData: 16010101000000.0Z
# search result
search: 2
result: 0 Success
# numResponses: 6
# numEntries: 5
Example 2 — Users in BOTH "windows AD" AND "Developers AD"
root@gateway:~# ldapsearch -x -H ldap://192.168.1.18 -D "CN=Administrator,CN=Users,DC=ezldap,DC=com" -W -b "OU=develop,DC=ezldap,DC=com" "(&(memberOf=CN=windows AD,OU=develop,DC=ezldap,DC=com)(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com))"
The output of the above ldapsearch command is shown below.
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <OU=develop,DC=ezldap,DC=com> with scope subtree
# filter: (&(memberOf=CN=windows AD,OU=develop,DC=ezldap,DC=com)(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com))
# requesting: ALL
#
# Gladwin, develop, ezldap.com
dn: CN=Gladwin,OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Gladwin
givenName: Gladwin
distinguishedName: CN=Gladwin,OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250924012727.0Z
whenChanged: 20250924012727.0Z
displayName: Gladwin
uSNCreated: 127613
memberOf: CN=windows AD,OU=develop,DC=ezldap,DC=com
memberOf: CN=Developers AD,OU=develop,DC=ezldap,DC=com
uSNChanged: 127621
name: Gladwin
objectGUID:: X6yQuoeC9EirR4np2gBYRA==
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 134031508473159222
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAytlsHZqhFKFfZ06wZAYAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: Gladwin
sAMAccountType: 805306368
userPrincipalName: Gladwin@ezldap.com
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=ezldap,DC=com
dSCorePropagationData: 20250924012727.0Z
dSCorePropagationData: 16010101000000.0Z
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
Example 3 — Users NOT in "Developers AD"
root@gateway:~#ldapsearch -x -H ldap://192.168.1.18 -D "CN=Administrator,CN=Users,DC=ezldap,DC=com" -W -b "OU=develop,DC=ezldap,DC=com" "(!(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com))"
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <OU=develop,DC=ezldap,DC=com> with scope subtree
# filter: (!(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com))
# requesting: ALL
#
# develop, ezldap.com
dn: OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: organizationalUnit
ou: develop
distinguishedName: OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250718111400.0Z
whenChanged: 20250718113159.0Z
uSNCreated: 12795
uSNChanged: 12808
name: develop
objectGUID:: uClkrmIPTECJ2RxLWw/RhQ==
objectCategory: CN=Organizational-Unit,CN=Schema,CN=Configuration,DC=ezldap,DC
=com
dSCorePropagationData: 20250718113159.0Z
dSCorePropagationData: 20250718111400.0Z
dSCorePropagationData: 20250718111400.0Z
dSCorePropagationData: 16010101000000.0Z
# Developers AD, develop, ezldap.com
dn: CN=Developers AD,OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: group
cn: Developers AD
member: CN=Gladwin,OU=develop,DC=ezldap,DC=com
member: CN=Renaud,OU=develop,DC=ezldap,DC=com
member: CN=Ronaldo,OU=develop,DC=ezldap,DC=com
member: CN=AlexGlobal,OU=develop,DC=ezldap,DC=com
distinguishedName: CN=Developers AD,OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250924004012.0Z
whenChanged: 20250924021039.0Z
uSNCreated: 127044
uSNChanged: 127629
name: Developers AD
objectGUID:: nyS1PBBO0kyDoAl3urev/Q==
objectSid:: AQUAAAAAAAUVAAAAytlsHZqhFKFfZ06wXwYAAA==
sAMAccountName: Developers AD
sAMAccountType: 268435456
groupType: -2147483646
objectCategory: CN=Group,CN=Schema,CN=Configuration,DC=ezldap,DC=com
dSCorePropagationData: 16010101000000.0Z
# windows AD, develop, ezldap.com
dn: CN=windows AD,OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: group
cn: windows AD
member: CN=Gladwin,OU=develop,DC=ezldap,DC=com
member: CN=Gerald,OU=develop,DC=ezldap,DC=com
distinguishedName: CN=windows AD,OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250924011635.0Z
whenChanged: 20250924012727.0Z
uSNCreated: 127064
uSNChanged: 127619
name: windows AD
objectGUID:: WN7sHYtEhEyWDSTdi1Yceg==
objectSid:: AQUAAAAAAAUVAAAAytlsHZqhFKFfZ06wYAYAAA==
sAMAccountName: windows AD
sAMAccountType: 268435456
groupType: -2147483646
objectCategory: CN=Group,CN=Schema,CN=Configuration,DC=ezldap,DC=com
dSCorePropagationData: 16010101000000.0Z
# Gerald, develop, ezldap.com
dn: CN=Gerald,OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Gerald
givenName: Gerald
distinguishedName: CN=Gerald,OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250924012140.0Z
whenChanged: 20250924014130.0Z
displayName: Gerald
uSNCreated: 127602
memberOf: CN=windows AD,OU=develop,DC=ezldap,DC=com
uSNChanged: 127624
name: Gerald
objectGUID:: OqYP+V0xjkOpBb8x5M2eAw==
userAccountControl: 66050
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 134031505005918452
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAytlsHZqhFKFfZ06wYwYAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: Gerald
sAMAccountType: 805306368
userPrincipalName: Gerald@ezldap.com
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=ezldap,DC=com
dSCorePropagationData: 20250924012140.0Z
dSCorePropagationData: 16010101000000.0Z
# developer, develop, ezldap.com
dn: OU=developer,OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: organizationalUnit
ou: developer
distinguishedName: OU=developer,OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250718113159.0Z
whenChanged: 20250718113159.0Z
uSNCreated: 12807
uSNChanged: 12809
name: developer
objectGUID:: 8aH/n5GlFEugQcPZoDjjdQ==
objectCategory: CN=Organizational-Unit,CN=Schema,CN=Configuration,DC=ezldap,DC
=com
dSCorePropagationData: 20250718113159.0Z
dSCorePropagationData: 20250718113159.0Z
dSCorePropagationData: 16010101000000.0Z
# search result
search: 2
result: 0 Success
# numResponses: 6
# numEntries: 5
Example 4 — Users in "windows AD" but NOT in "Developers AD"
root@gateway:~#ldapsearch -x -H ldap://192.168.1.18 -D "CN=Administrator,CN=Users,DC=ezldap,DC=com" -W -b "OU=develop,DC=ezldap,DC=com" "(& (memberOf=CN=windows AD,OU=develop,DC=ezldap,DC=com) (!(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com)))"
The output of the above ldapsearch command is shown below.
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <OU=develop,DC=ezldap,DC=com> with scope subtree
# filter: (& (memberOf=CN=windows AD,OU=develop,DC=ezldap,DC=com) (!(memberOf=CN=Developers AD,OU=develop,DC=ezldap,DC=com)))
# requesting: ALL
#
# Gerald, develop, ezldap.com
dn: CN=Gerald,OU=develop,DC=ezldap,DC=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Gerald
givenName: Gerald
distinguishedName: CN=Gerald,OU=develop,DC=ezldap,DC=com
instanceType: 4
whenCreated: 20250924012140.0Z
whenChanged: 20250924014130.0Z
displayName: Gerald
uSNCreated: 127602
memberOf: CN=windows AD,OU=develop,DC=ezldap,DC=com
uSNChanged: 127624
name: Gerald
objectGUID:: OqYP+V0xjkOpBb8x5M2eAw==
userAccountControl: 66050
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 134031505005918452
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAytlsHZqhFKFfZ06wYwYAAA==
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: Gerald
sAMAccountType: 805306368
userPrincipalName: Gerald@ezldap.com
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=ezldap,DC=com
dSCorePropagationData: 20250924012140.0Z
dSCorePropagationData: 16010101000000.0Z
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
List Enabled User Accounts (LDAP filter for enabled accounts):
root@gateway:~#:~# ldapsearch -x -H ldap://192.168.1.18 -D "CN=Administrator,CN=Users,DC=ezldap,DC=com" -W -b "OU=develop,DC=ezldap,DC=com" "(&(objectClass=user)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))" sAMAccountName mail
The output of the above ldapsearch command is shown below.
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <OU=develop,DC=ezldap,DC=com> with scope subtree
# filter: (&(objectClass=user)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))
# requesting: sAMAccountName mail
#
# AlexGlobal, develop, ezldap.com
dn: CN=AlexGlobal,OU=develop,DC=ezldap,DC=com
sAMAccountName: AlexGlobal
# Ronaldo, develop, ezldap.com
dn: CN=Ronaldo,OU=develop,DC=ezldap,DC=com
sAMAccountName: Ronaldo
# Renaud, develop, ezldap.com
dn: CN=Renaud,OU=develop,DC=ezldap,DC=com
sAMAccountName: Renaud
# Gladwin, develop, ezldap.com
dn: CN=Gladwin,OU=develop,DC=ezldap,DC=com
sAMAccountName: Gladwin
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 4
List Disabled accounts only:
root@gateway:~# ldapsearch -x -H ldap://192.168.1.18 -D "CN=Administrator,CN=Users,DC=ezldap,DC=com" -W -b "OU=develop,DC=ezldap,DC=com" "(&(objectClass=user)(userAccountControl:1.2.840.113556.1.4.803:=514))" sAMAccountName mail
The output of the above ldapsearch command is shown below.
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <OU=develop,DC=ezldap,DC=com> with scope subtree
# filter: (&(objectClass=user)(userAccountControl:1.2.840.113556.1.4.803:=514))
# requesting: sAMAccountName mail
#
# Gerald, develop, ezldap.com
dn: CN=Gerald,OU=develop,DC=ezldap,DC=com
sAMAccountName: Gerald
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
Related Articles:
How to create filters in Ezeelogin while using LDAP or AD authentication?