Setup LDAPS on Windows server
How to configure LDAP over SSL (LDAPS) on Windows server?
Overview: This article explains how to set up LDAP over SSL (LDAPS) to create a secure, encrypted connection between the LDAP server and Ezeelogin.
Steps to secure Active Directory / Configure LDAPS
1. Install Active Directory Certificate Services (AD CS)
2. Create certificate template
3. Issue certificate template
4. Request new certificate for created certificate template
5. Export the created certificate
6. Configure LDAPS on the gateway server
Detailed Step-by-Step instructions
1 Install Active Directory Certificate Services (AD CS)
Step 1(A): On the Windows Server Machine, click on Start -> Server Manager -> Add Roles and Features.
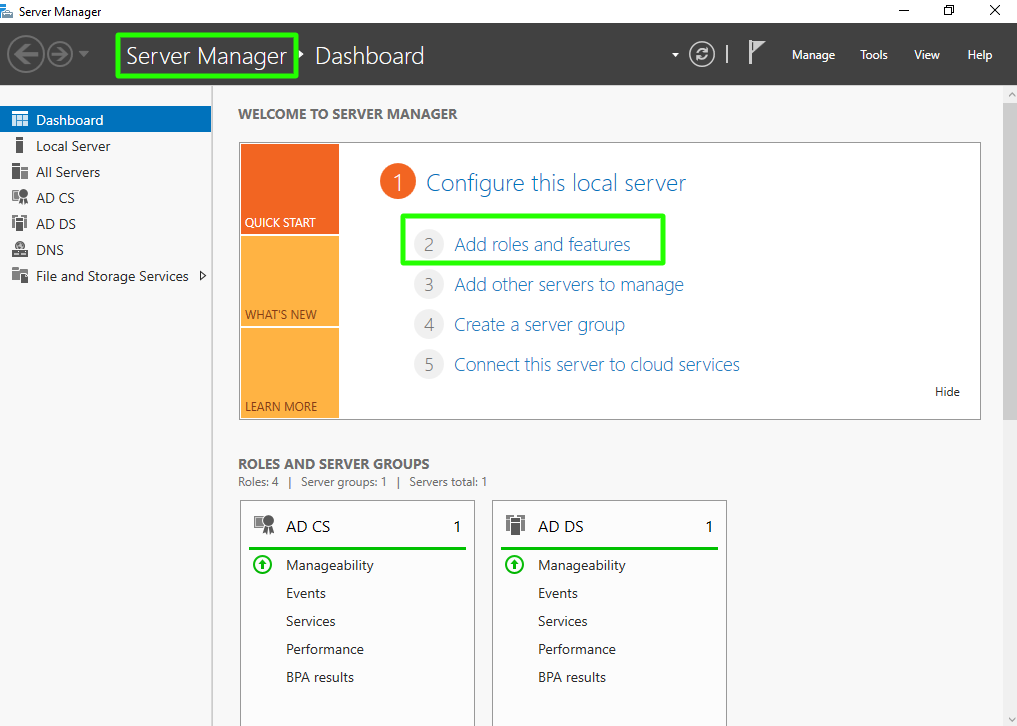
Step 1(B): After selecting Add Roles and Features and Click on Next.
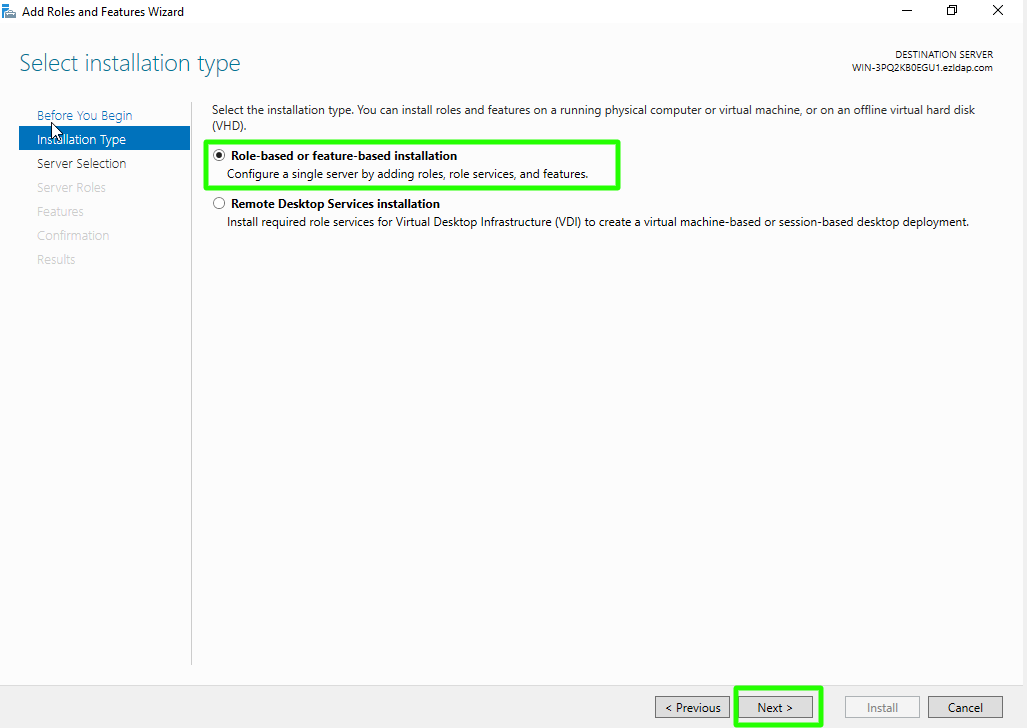
Step 1(C): Choose "Role-based or feature-based installation" option and Click on Next button.
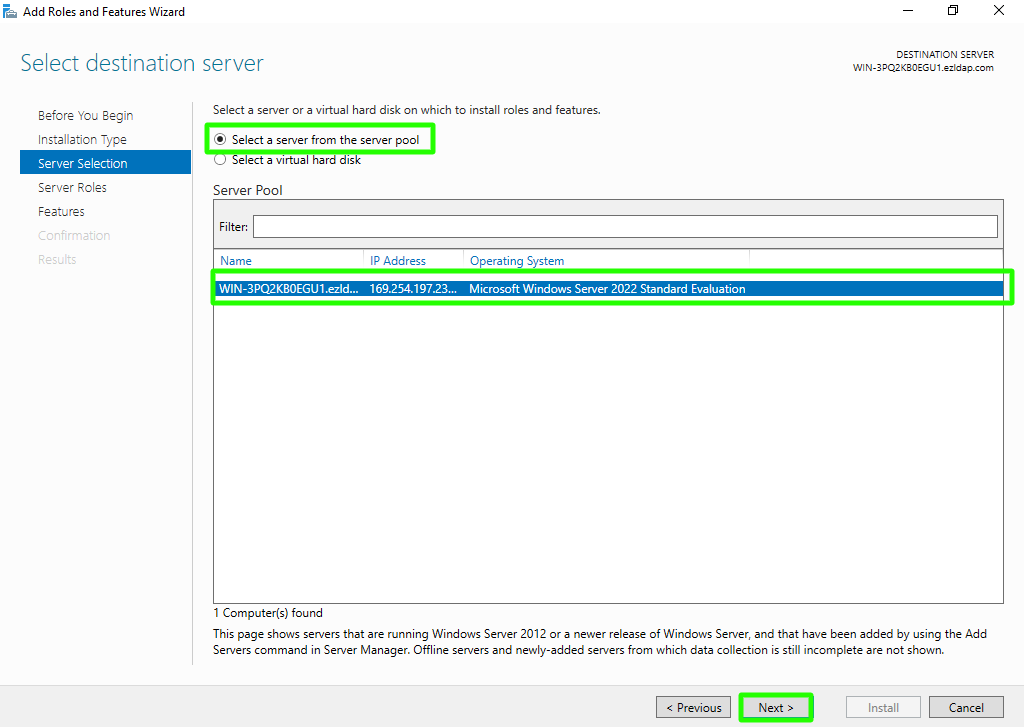
Step 1(D): Choose "Select a server from the server pool" option & select the ldap server from the server pool and click on Next button.
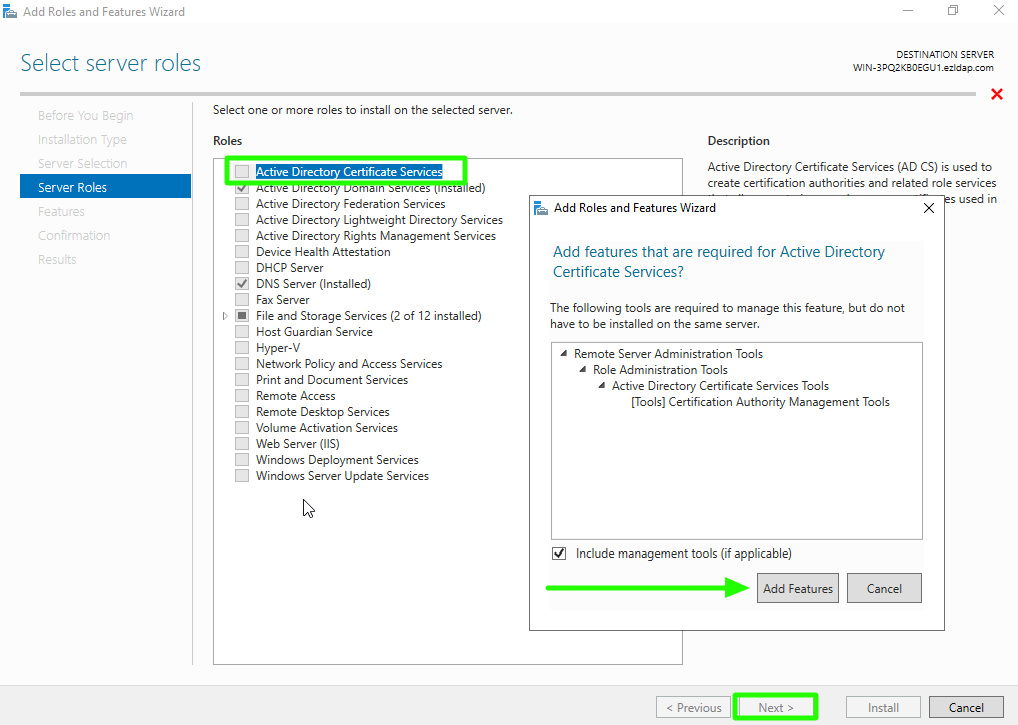
Step 1(E): Select "Active Directory Certificate Services" from the list of roles, then in the next window, click "Add Features" and proceed by clicking Next.
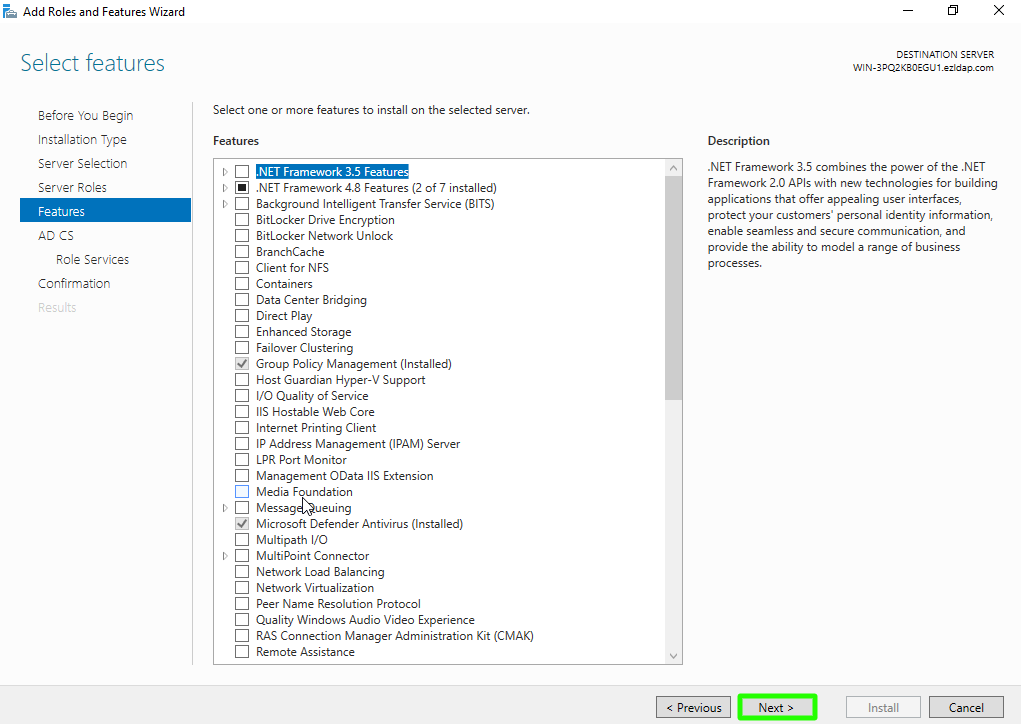
Step 1(F): Choose nothing from the list of features and click on Next button.
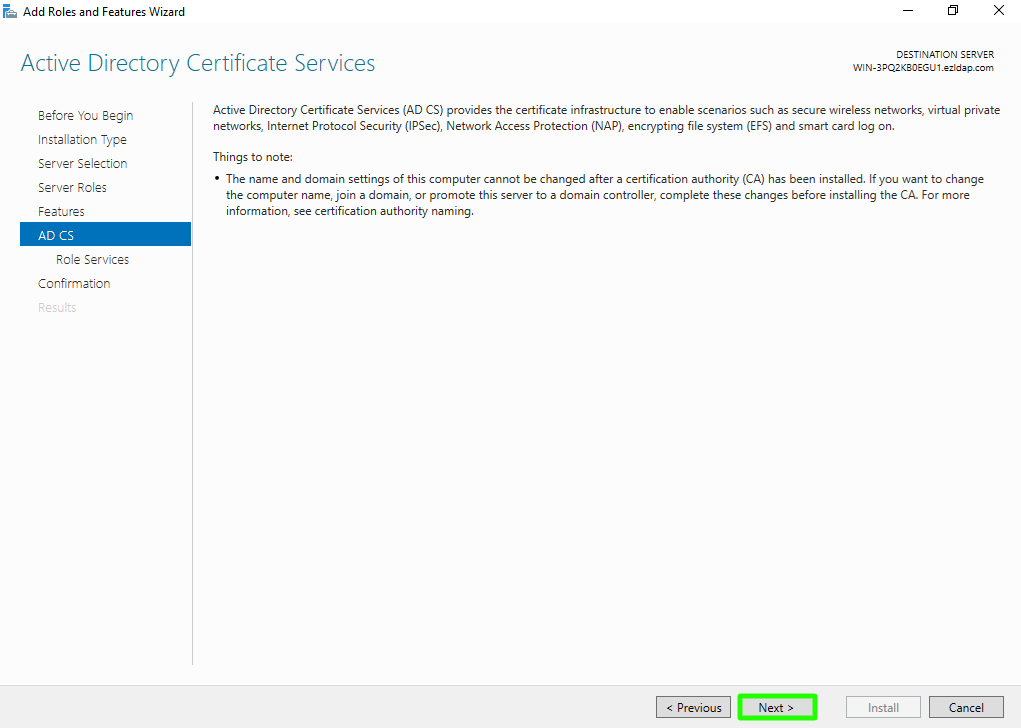
Step 1(G): In Active Directory Certificate Services (AD CS) choose nothing and click on Next button.
Step 1(H): Enable "Certification Authority" from the list of roles and click on Next button.
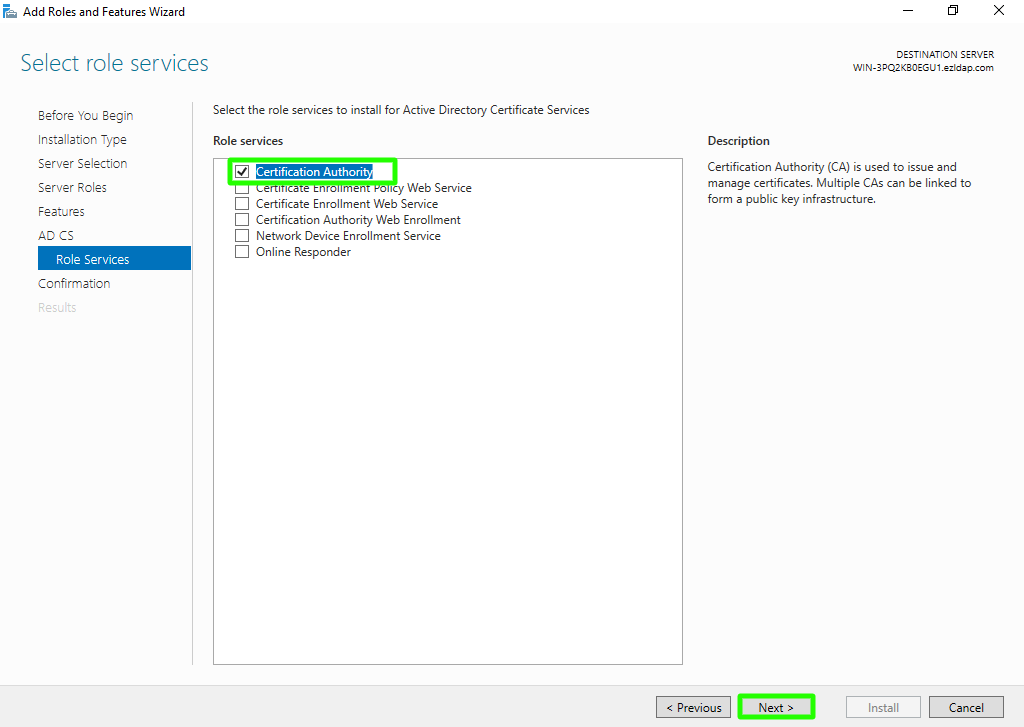
Step 1(I): Click on install button to confirm installation.
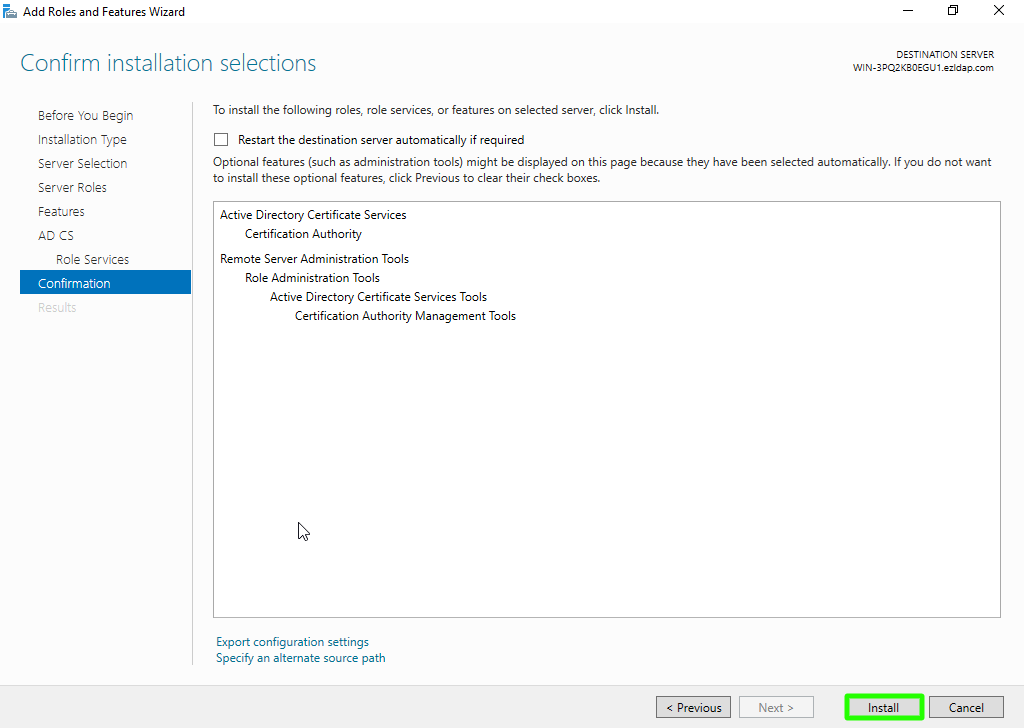
Step 1(J): Wait for the process to complete, then in the next window, click "Configure Active Directory Certificate Services on Destination Server", and finally, click Close.
Step 1(K): Use the currently logged on user to configure role services and then click on Next button.
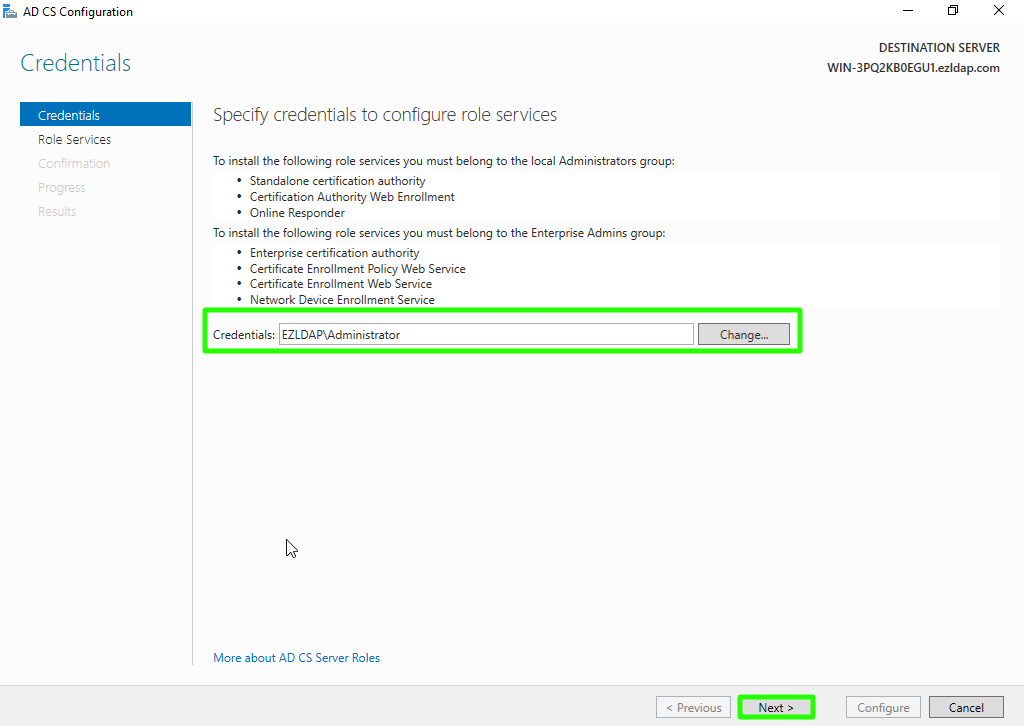
Step 1(L): Enable "Certification Authority" from the list of roles and Click on Next button.
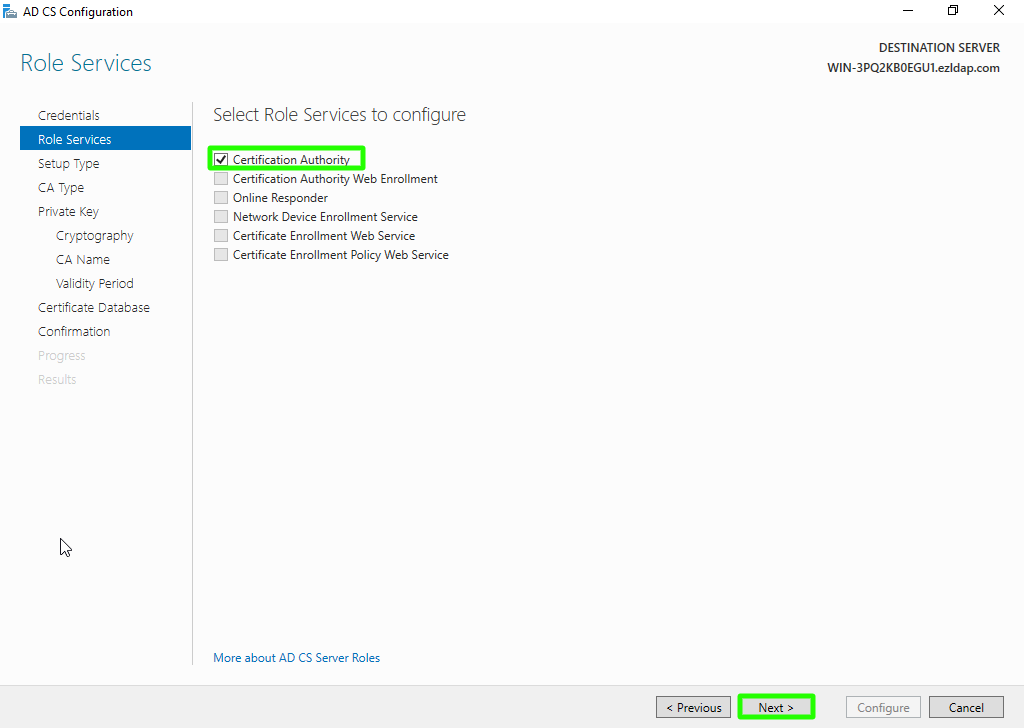
Step 1(M): Choose "Enterprise CA" option and click on Next.
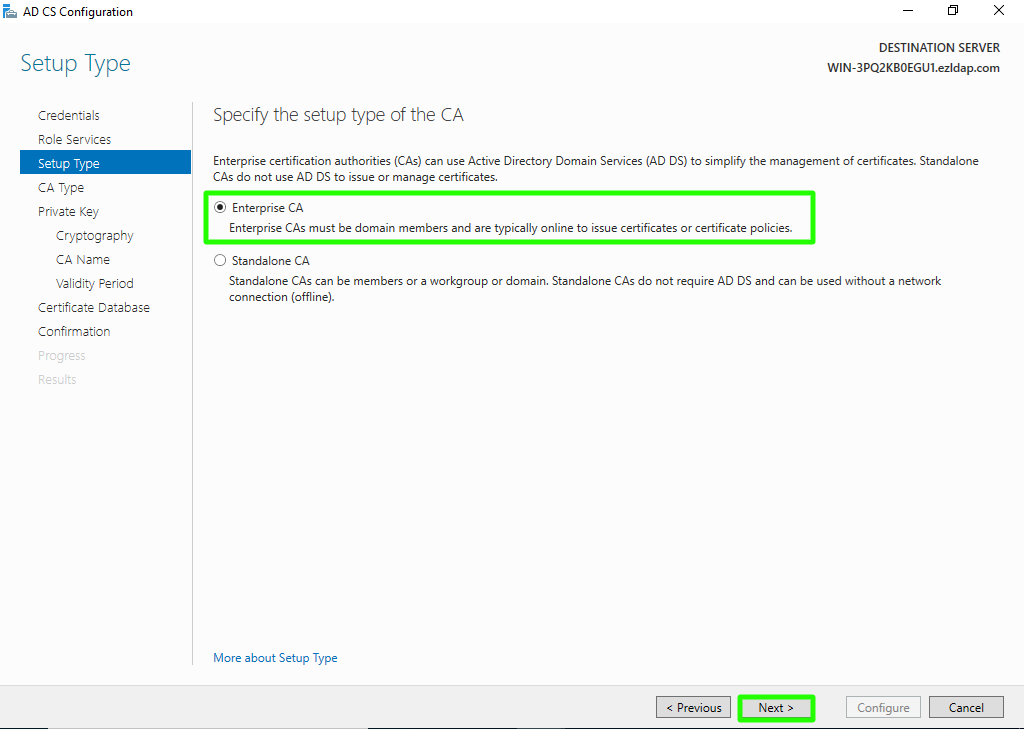
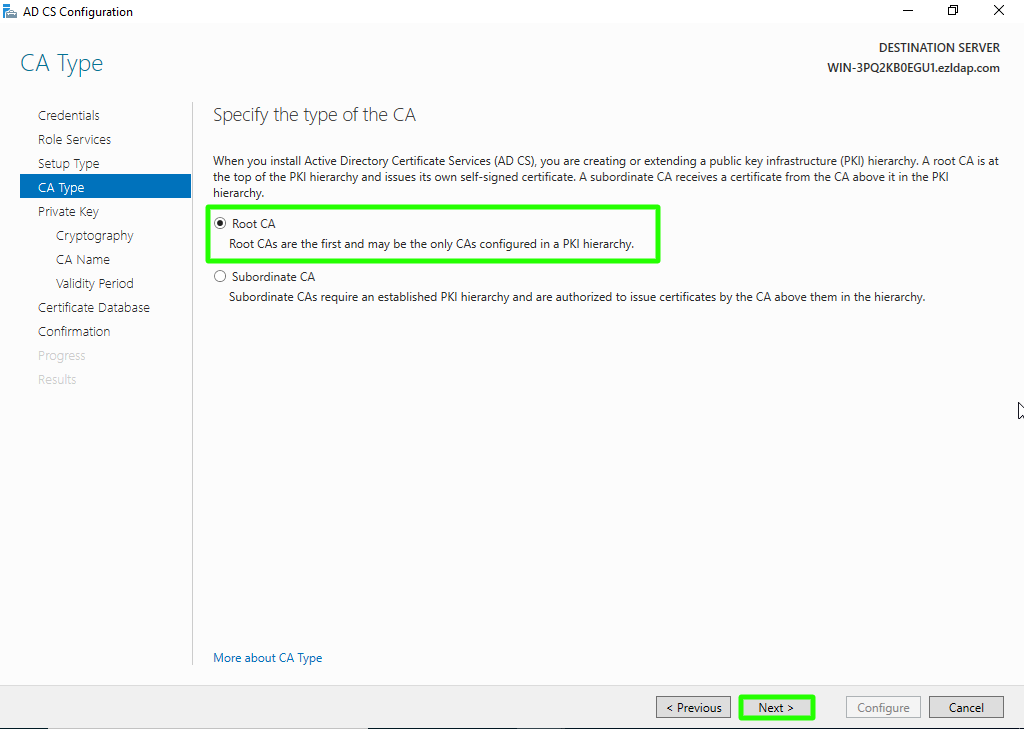
Step 1(N): Choose "Root CA" option and click on Next button.