Encryption Technologies used in Ezeelogin
What are the Encryption algorithms used in Ezeelogin?
Overview: This article outlines the encryption technologies used for SSH gateway users.
The user passwords and security codes stored in the gateway server database use multiple rounds SHA512, SHA256, BLOWFISH, or DES depending on what's supported in the SSH gateway OS.
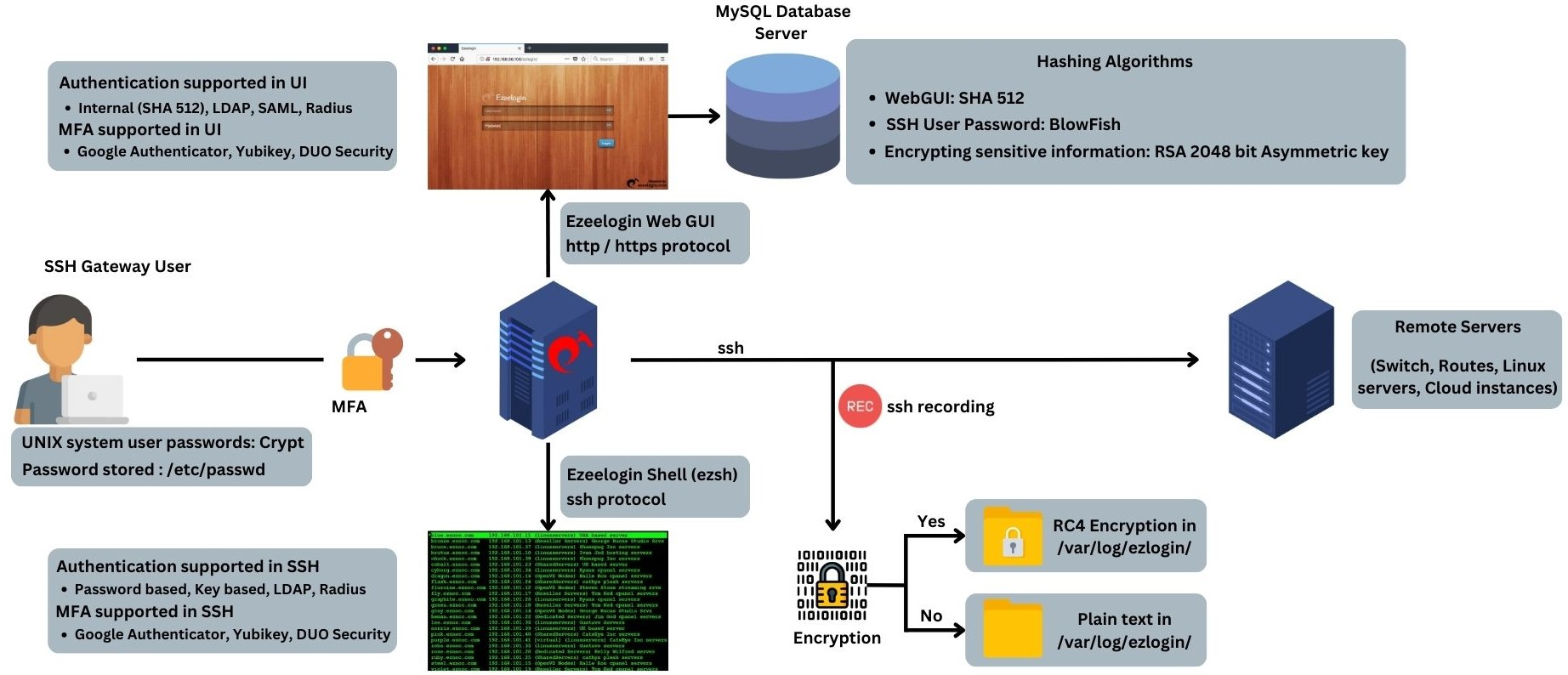
The UNIX System User passwords uses Crypt.
The parameter after the " : " in /etc/shadow refers to the hashing function in use.
User credentials on the database are encrypted.
mysql> select username,password from mvsxzv_users \G
*************************** 1. row ***************************
username: ezadmin
password: $2y$10$G769haw9EJ02j66GAoHZu.e5eWNTNpg4zeSG8FaG51T7ZC0Mv6rlC
*************************** 2. row ***************************
username: manu
password: $2y$10$J8YCqVSWZ/OOxjJmr61DMuhte3EPWpsx580xBDY.62x9nNa5V1Kgu
*************************** 3. row ***************************
username: mark
password: $2y$10$UPmd24lNFFM9uUneYM4y4eJIDzCRLbP/FXMWJXn/Gxsy4ZlRlksSG
*************************** 4. row ***************************
2. The SSH private keys, server credentials are encrypted with 4096 bit RSA keys.
mysql> select name,password,ssh_key,passphrase from mvsxzv_servers \G *************************** 1. row *************************** name: devops.myserver.com password: GnfZwSNlLF3XOAQg2czY4Y7AsezNTm0/+40bd0o6KjX7hgaD0OoV71wB1eihBbNFHfAYQ5YstsWCKil9/h7VYPp9eGi2Kbsa7OzLFta3jpG/Xm6GdSqJLOslBI/oyU44TQUfUhb1eW+NM+hInAYAASft5LWoVUlWOwl+sE16cLraOwvfoLzz7TQvVg4YOekBYLDJqtOzVLCe4KIQbT1fb19Ei0Gm5p9Z/DHoh3wAFvk8WoNdrjOuSX6mO0A+SToYU5Bu+tPJC4WRl4hmOxo94HB1GRlzydHKRN5OwCkP9LhhbgXayc0FYiu801VI82sXm2/dZ0MMuCelFe+trBHyGw== ssh_key: uLhhwBHLwNxWwNEAY9iG7gqwx8uzLRqBsOWSf/yt1eQ6HW4D4IJK7NZRNK9Ry3Ux5MZOaX+nKyV8JFyw0sBXLDE031D4gIMhSxjw5UA2FXhOAOk2EMzsdY4qei4Wl9Ma6XQVyNG9Cg+cEQDE9vuOMG5okXR+FK+4iw46GB7tiByPPvrXAdrrpw9WDQSBvhtopa7b/nXi9yW3FdhHBvRY465ciI2eja3rujcVIwuMNM7keRGReqpYsglrZhRhdxkpWNRlDIfuOuHQQas0L8ZkgHTlWZBJc36BkjNTaFtwcTkZwKkgTx+F1/eCQJax/7qfOB/ih4AcB5t1m582sIU07MaBFA1DamODYblUBa8T1rAZqXpwJUtdHWByAWwregtw0Zmc8dFFnt5MxJp5/eZii4ViJYGrhmdSmHYFJnvwJt5DoBZDBdN+EpEpvu4lRKF2KdtwB0kp5wT3MOaTc4EZ7XeUKj3Hfsltp/c0hInEynaZrQZ28uG5n6aaEedvUreFTA6b4CygDqvDVXOXWWIW6+j3fa0SnyhbJnJnucqUIQQds+Bfg0naoKs0ehpxdxbqX7RQU6SS3p/0MjpZwwSWugCc1lKVAtLeGo+SqK5UvXTMlE6s05cxm4VTP4QxkSg3bapO4GPyHBh553Dol8R3c2+oGpw0BL0yE+ArYA9lQm/NVjN84hBxPjNnGEDDsPA+4kSRumosELIgF3QcGfqh8SUL6IP5pf8SPwY1K833vbKSsp1hXMEmNTuqjDsAqHM/KeyubZkoAKBErCMaCUPRoOyBxMR50y6NTPSsxujz67wEEGeLeC41tRxvOMmuVpbMuKCHo3dY1/l9G9LBPOJ1WIsLo2E+3iGLALgR9Mfr4CuWmDv+qMcMgQUel6VY7Be1SgybrlAAYm4WQ3zGijB+xTK90hWKpZi/YgtwmogQAwO5aYzpTIap7/WQvaZi88UbZ/MLOJalMJJXAudI8IXvUd+nVuvkyqXehzArOlo1VVNiYKETQzbebIBp9BRE+v8niLx8b25TeRGSuADOjPMbFIo0PQPWf0nKxuD/JrCxuva2fgGzzrj0JjIODwWgakKM9fMvb5oC510/c5e1biXSrzaX+Lifu5WlSLJLA/ZYIdsfuaJ3RB45NVXdJnMlD0Qzyru7FIod3GSdI0/FkSfrgrPshK5pmR4Cnj9kopBkYhlGxdIiQ+BaIyAnXVIGybVmsi8tqYHMsrYVdyzKCeGnZyK82xbO1PgspVlOFBiTExnCGkyvbyatge+dUbcqHytR+UW0BN2qHZkNxuHSDC/RglAUM5muzE3m+kIYSAGZm0mcUAHUXxAzWfhoVwYX0VBImkJ3thGV5W2+3KfzjgHQjOT7CJqX5s+3HRuGkV6tCErBbl5MaquOioasPIQ49bphvoWE9Umcx4HstXtJiiFJpecmNR0BrRdYyNNkUgtFZ8YjLPX2Ratnl2Loh/t7zvvZ/rLdOhNwEO5kOw9eHiiFSMr3ODCTkpCP/xbzAepMTCW+TtLl6cULZqlw385TlR7EdS6aWIaK6AgYh+cv/jcDg6dMiQs+sN8t/1AzZcijRH6slqYtrinNOHqTPOre1M4skTrFlXzfZUmkljc5G3O+9ZGh30TaU0q2IuHkGvZJ1QspznLVYU+hZDtEFo2xD6wqtOxyJrJdj6YRvfYt64alvWNckFKlj1J0T62IS1V2OvzRghG3SYJC0/QKUbIPu3R1O4c0rDWNQ9Rphd56CBLhkuEiQ6bGAsi4x53+ZRN3CQtjdjOJTl07j5UY3/E9dp+Cis0UAGOng4PWmNdGt1xtoUGSeg2Y3lCYndeDn+Twrth+DKFxGzFDdw/xWi8zhxXxGr6ymeC2FJOFzQZUzQAZ5K02FO/G8jLpTLu7hVHMkUD1Ye1dHG58yY72QvTV6XO6vHgB5hdbgx38ffdDGYZ7Cvw9p0RJRDW7iJO0VumjC3L+mh7w1pxtfq2rDTUiXAu7vDIgWZY0P7npxS5eAURbXM8D2uQLudki9rwCaOO2BBUyJd1Kj+uXNxwqcXBwhwS0wXm/gDw2Wfcc/bN3hKGfF9YWscznVnIx9JeQRZNI91I9WoZQM5VJ2sXP2rxYEh423jaEC6ZMaLo+sG2mNuRpFWeLq+mEDxbMm3bk4thTX4grDcLdvxQC+4EblEZZ22jiNkdeknMn1RGsbS92AIZDk4qeWZyK4nRqfeKhhnABJ8Qxy643vhP5naz1tDmoa+VxBSgbCPnPiHnURL7D50Qj6s8CQecVuU9exeCgfqeGnS274Sff+MAZMfNSEnHTtwUMK0e+QckgPbhqkA1GUyM26PLpW1DPuWl5vVpOLRwhUQdI4oqjXpSssP8dHoL6ODmG7IJRkj5Ny8HOYH5+n+Tj3azEJ4rqs/CTIg4OUkVKKgNCKd4gk2gHK6Z2t8Gec5boQVAOhfm5oqTK+4JO3DYhlIQmGc7t+HQIuDyv3U2TmVGcXaAO6Md6y4A2np0TQRuAyOiiMwJXTvoagGGIo8kD3JLaR7Jn2ysSShFjGo/wfIbs+0zfp8wDlPxZV1d0p+G33UkSCx+7QlKqZnep03it3hDempJRSq1tQSlmWjmx/WpdCXOYblyRrCaDSSKwCuuN5ZRn5lD9pilit4/SAD2t79YJeH8V1/EW3LtTPcPXGXaOJVPYCqJ+2/2v7r6fMZXZQDGbZ+tekXFiUeO4MqmKOC/+p5eJwnnFP7WN6iU1OVp+GLb+VclcKFHgtdL0tr9KJClxW5XXL6xY2BWksGxHDV6eECs7HeYZxSJVl+S2uF54HHJ9MRqVD4eqm+75u1ShkF+R/2kMHMzmg/3yNvocz/4bz5RkixTys6RylSdAcYnoz1kvqZHJF37MNQcK20smQE8TZkQrsGGcZ5eCO7bb9l2mO9qa999Wwel2fga+RJZp5E+UbDfrO0UVeNuuQsTp1Pmno8njTQ2KpFBFgbOPA1HVWLfyTBlQq6X9+N6gB3V476cXXOtM2y1rVA== passphrase: GFRtZHNOPiJx46Q2DZiwi0NlFEH1b8h4MA1/KOHko5ypmdP8zlfHByb4vqTCoFFBQ+IAgOKmjL8m3J2/2tBfKFLT6lGf7fFH1fTeulg6t5yAUDYfvaYvFFP/zYoO6JO8vO9YJBQJhNtJkVVOhei3ILqz5LnFzE/EwNOCr35spUq2PJ5M+4XeSp3P6pGXoux3qE+Otp/OKJVP21cWfqEgaxHiNnH1OqzrDeKKeoYakjjdFT8z7Bd58MGXlyNq/W+S97Clodz4Yv1U1FrGH2pBxzNnLpsKFU4yV8PPVltxsRfVSw8KPJ4tkAGINs97J90eXkcO4Ohat8hlsqRBKpDuwA
========== 1 row in set (0.00 sec)
3. Web portal login credentials are encrypted.
mysql> select name,username,password from mvsxzv_portals \G
*************************** 1. row ***************************
name: cpanel.ovh
username: admin
password: JOJug8WaJN8VRRWtb7dRTR+D2BSZYP/WPsoSx0YeVMv7odSJox+5a713SHrR6AJ31YVtDEBPpWNwlyK/83es3J+plI5TceKGZhUp0WhRtrLsGEMW07uvDrq8XI2DK3n1Wzz4xrpXKBLOhmixK+nbB59J/CTeqwd3oaRSFOHaAUa1XLghyBtiHC/wyJcgLH06nof61+0Hvwe+WaPTa7uW4L2gWZ0OSeEt4xDMSU/6Gqo7JzNqLPFNf8CPSrsKZHNyEzkrza+kneT2rjvKbZc0gUyEBhocMCRz7uhGj/YV0HjoG/qncl9EzRa1IazhVlsnPZrwfLpsAQtvFVGYCfqOow==
1 row in set (0.00 sec)
4. The Gateway User SSH logs are encrypted using RC4 which is recognized as the most commonly utilized stream cipher in the world of cryptography. You may read more about RC4 http://en.wikipedia.org/wiki/RC4
Step 4(A): Run the following command to find the default Ciphers, MAC , Kex Algorithms supported in the gateway OS.
SSH logs are stored in an encrypted format within the database, as depicted below.
Related Articles:
Encryption type used for securing users' SSH logs in ezeelogin