Token encryption in Microsoft Azure SSO with Ezeelogin
How to enable token encryption in Microsoft Azure for SAML authentication?
Overview: This article helps to enable token encryption in Microsoft Azure for SAML authetication.
Refer article to integrate Microsoft Azure SSO authentication in Ezeelogin.
Step 1: Create a new private key
root@gateway:~# openssl genrsa -out key_name.key key_strength
EXAMPLE
root@gateway:~# openssl genrsa -out private_key.key 2048
Step 2: Generate a certificate signing request (CSR) associated with your private key.
root@gateway:~# openssl req -new -key path_to_private_key.key -out csr_name.csr
EXAMPLE
root@gateway:~# openssl req -new -key private_key.key -out CSR.csr
Step 3: Convert .csr (Certificate Signing Request) file to a .cer (Certificate) file.
root@gateway:~# openssl x509 -req -in yourfile.csr -out yourfile.cer -signkey yourfile.key -days 365
EXAMPLE
root@gateway:~# openssl x509 -req -in CSR.csr -out CSR.cer -signkey private_key.key -days 365
Step 4: Download the certificate to your PC.
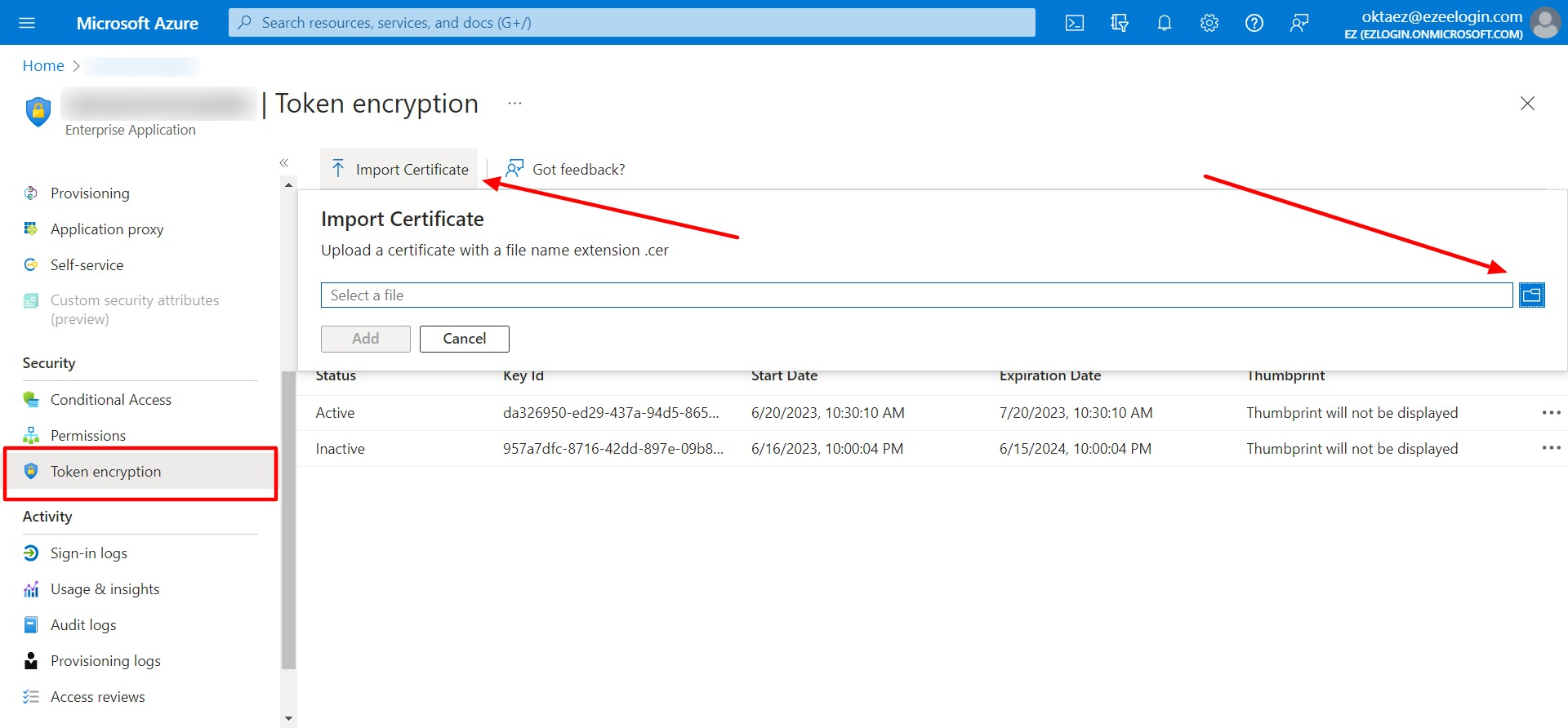
Step 5: Click on Token encryption on your Enterprise application. Click on import certificate and import the certificate file from your PC with the .cer extension.
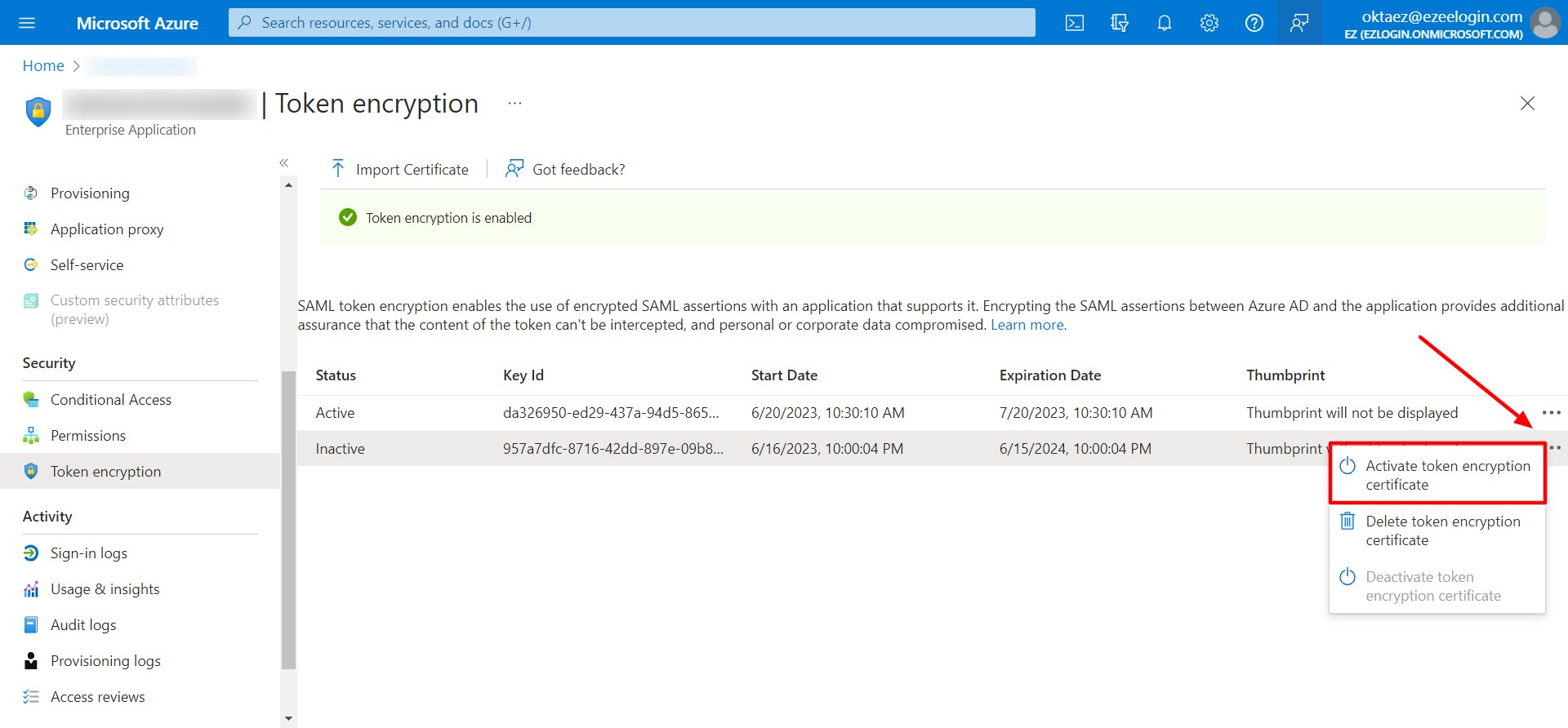
Step 6: Activate the certificate by clicking on three dots and Activate token encryption certificate.
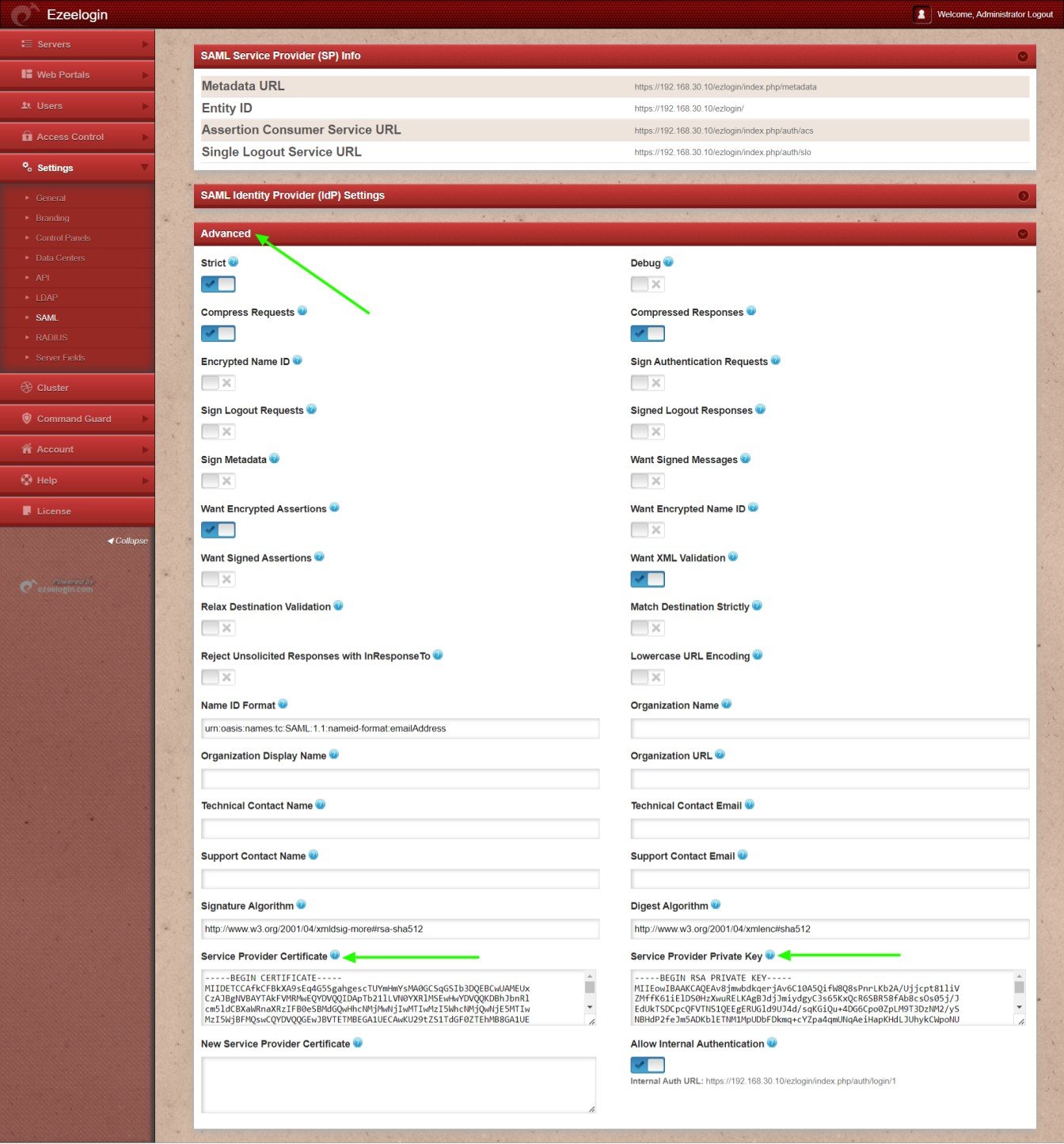
Step 7: Add the certificate and private key to Ezeelogin SAML advanced settings.
Use the certificate and private key in Service Provider Certificate and Service Provider Private Key.
Enable Auto Create and change web panel authentication to SAML. Clear the browser cache and try to log in to Ezeelogin with Azure login credentials.
Common errors while accessing Ezeelogin with Microsoft Azure token encryption configured
No private key available, check settings
This error happens because Service Provider Certificate or Service Provider Private Key field is empty.
Key is missing data to perform the decryption
This error happens because the private key saved in Ezeelogin is different from the key used to generate the certificate used in Azure token encryption.
Related Articles:
Integrate Microsoft Azure SSO and AD with Ezeelogin
Unable to login with Azure SSO
Integrate GSuite SSO with Ezeelogin
Integrate Jumpcloud SSO with Ezeelogin
Integrate AWS SSO with Ezeelogin
Integrate Okta SSO with Ezeelogin