Unable to add server using putty private key key pair. How to convert PPK file OpenSSH format
Issue with Adding Servers Using Putty Generated Private Key Pair (PPK)
Overview: This article describes how to convert Putty-generated private key pairs (.ppk) to OpenSSH format for compatibility with Ezeelogin and other systems.
The putty key is currently not supported in Ezeelogin. You have to convert it to OpenSSH format.
To convert to OpenSSH format, you can use PuttyGen.
Step 1: Download and Install PuttyGen
- Visit http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html and download PuttyGen.
- Install PuttyGen on your system.
Step 2: Open PuttyGen and Load Your .ppk File
- Launch PuTTYgen.
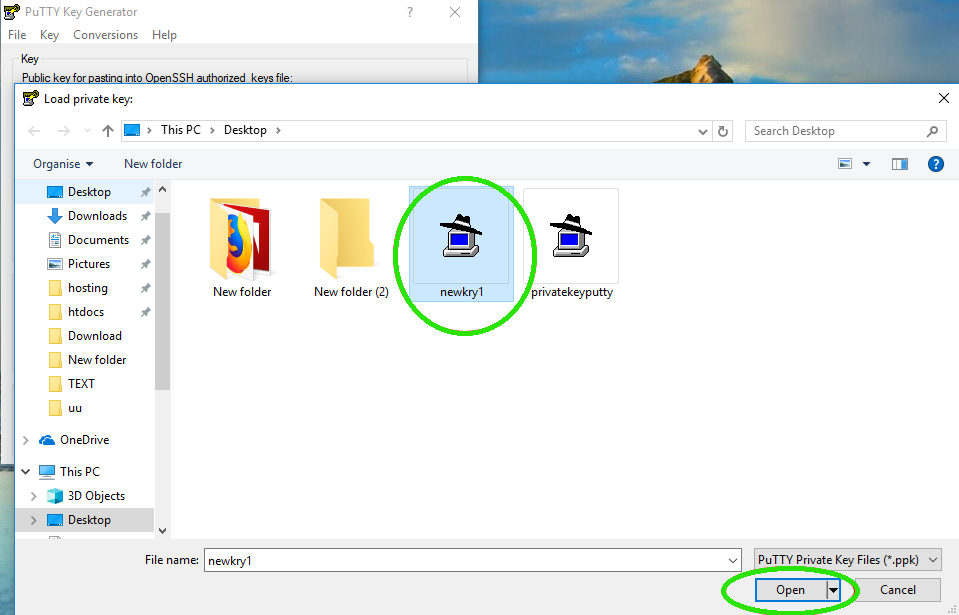
- Click on "Load" under Actions.
- Navigate to your .ppk file and select it.
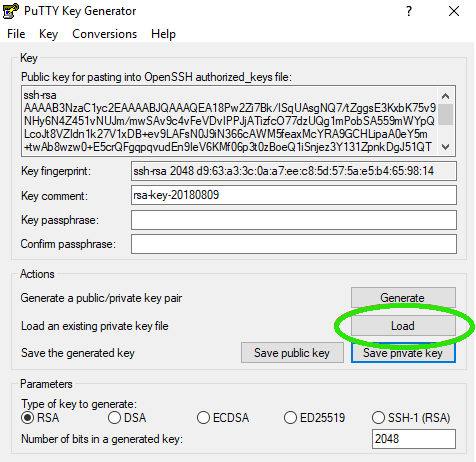
- Click "Open" to load the file.
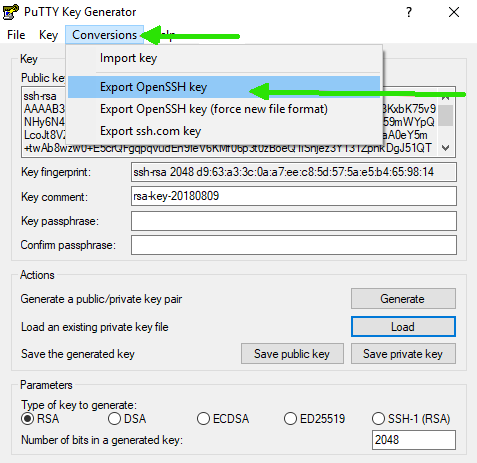
Step 3: Export the Key in OpenSSH Format.
- Once the key is loaded in PuTTYgen.
- Go to Conversions in the top menu.
- Choose Export > OpenSSH Key.
Step 4: Confirm Export Without Passphrase
- PuTTYgen may warn you about saving the key without a passphrase. Click "Yes" to proceed.

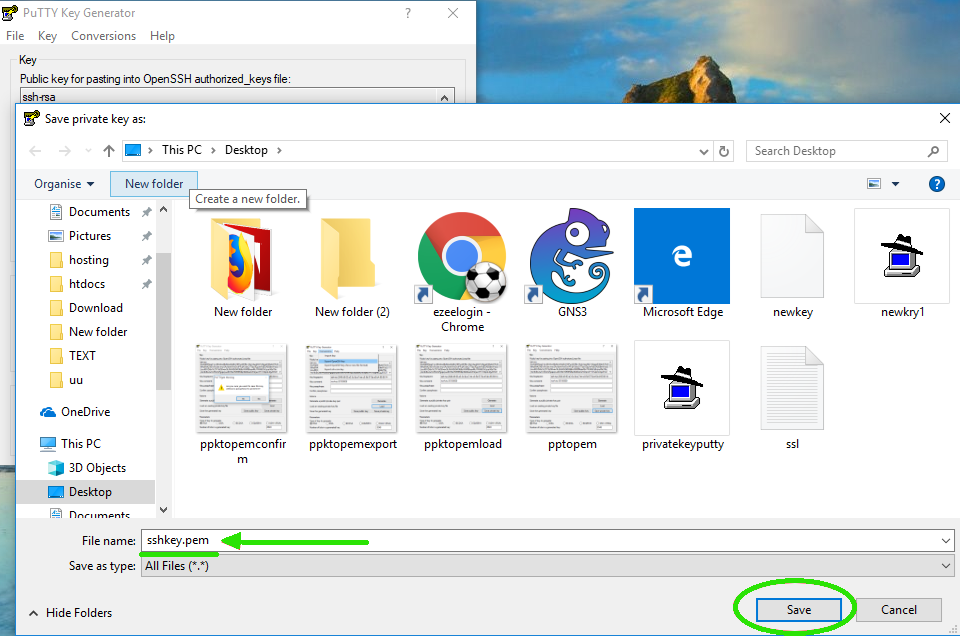
Step 5: Name and Save the Key
- Name the file as desired and add the .pem extension (e.g., mykey.em).
- Choose the location where you want to save the file.
Step 6: Convert Using Command Line (Unix/Linux)
- If you prefer using the command line on Unix/Linux:
- Install PuTTY tools if not already installed:
RPM-based (CentOS):
root@desktop:$ sudo yum install putty
Dpkg-based (Ubuntu/Debian):
root@desktop:$ sudo apt-get install putty-tools
- Convert the .ppk file to .pem format using puttygen.
root@desktop:$ sudo puttygen ppkkey.ppk -O private-openssh -o pemkey.pem
Related Articles:
Connection was closed by the remote host in Putty.